Information security management system of a corporate network
Міністерство
Освіти та науки, молоді та спорту України
НАЦІОНАЛЬНИЙ
АВІАЦІЙНИЙ УНІВЕРСИТЕТ
Кафедра
Комп’ютерних систем та мереж
ДОПУСТИТИ ДО ЗАХИСТУ
Завідувач кафедри
_______________ Жуков І.А.
“____”_______________ 2011
ДИПЛОМНА
РОБОТА
(ПОЯСНЮВАЛЬНА
ЗАПИСКА)
ВИПУСКНИКА
ОСВІТНЬО-КВАЛІФІКАЦІЙНОГО РІВНЯ “МАГІСТР”
Тема:
«Система управління інформаційною безпекою корпоративної мережі»
Виконавець: студент спеціальності 8.091501 Домарєв Дмитро
Валерійович
Керівник: д.т.н. проф. Віноградов М.А.
Консультанти з окремих розділів:
Нормоконтролер: Клименко І.А.
Ministry
of Education, science, youth
and sports of
Ukraine
NATIONAL
AVIATION UNIVERSITY
Computer
Systems and Networks Department
Permission to defend granted
Head of the Department
______________ Zhukov I.A.
“____”_______________ 2011
Master’s degree thesis
Topic:
“Information security management system of a corporate network”
Completed by: student of speciality 8.091501 Domariev Dmytro:
Doctor of technical sciences professor Vinogradov N.A.
Advisers on Individual Sections:
Standards Inspector: Klymenko I.A.
НАЦІОНАЛЬНИЙ
АВІАЦІЙНИЙ УНІВЕРСИТЕТ
Факультет
Комп’ютерних систем
Кафедра
Комп’ютерних систем та мереж
Освітньо-кваліфікаційний рівень: магістр комп’ютерної
інженерії
Спеціальність: 8.091501 Комп’ютерні системи та мережі
ЗАТВЕРДЖУЮ
Завідувач кафедри
_____________ Жуков І.А.
“____”_____________ 2011
Завдання на виконання дипломної роботи
П.І.Б. випускника:
Домарєва Дмитра Валерійовича
1. Тема дипломної роботи: «Система управління інформаційною
безпекою корпоративної мережі»
затверджена наказом ректора від « 15 » квітня 2011р. № 749
. Термін виконання роботи: з 15 квітня 2011 р. по 26 червня
2011 р.
3. Вихідні дані до роботи: При розробці концепції системи
управління інформаційною безпекою корпоративної мережі керуватися галузевими
стандартами Національного банку України та міжнародними стандартами ISO/IEC.
Застосувати системний підхід до оцінки ефективності системи управління
інформаційною безпекою. Розглядати систему управління інформаційною безпекою як
стохастичну систему з частковою керованістю і спостережуваністю.
. Зміст пояснювальної записки: Аналітичний огляд управління
інформаційною безпекою в корпоративних мережах; Огляд стандартів з управління
інформаційною безпекою; Огляд існуючих вирішень (продуктів); Математична модель
системи інформаційної безпеки; Визначення ефективних характеристик системи;
Покращення, забезпечені системою; Структура системи; Робота з оболонкою та
використання головних функцій.
. Перелік обов'язкового графічного (ілюстративного)
матеріалу: Логічне дерево виведення оцінки рівня безпеки; Розв’язання проблем
аналогічних продуктів; Схема бази даних системи; Витяг з політики інформаційної
безпеки, що формується системою; програмні модулі спеціальних функцій (тексти
програм).
.
Календарний план
|
№пор.
|
Етапи виконання
дипломної роботи
|
Термін виконання
|
Примітка
|
|
1.
|
Науково-дослідна
практика
|
17.01.11-13.02.11
|
|
|
2.
|
Переддипломна
практика
|
14.02.11-06.03.11
|
|
|
3.
|
Аналіз поточного
стану проблеми
|
07.03.11-20.03.11
|
|
|
4.
|
Розробка вимог до
системи
|
21.03.11-10.04.11
|
|
|
5.
|
Складання опису
пропонованої системи
|
11.04.11-30.04.11
|
|
|
6.
|
Оформлення
пояснювальної записки
|
01.05.11-29.05.11
|
|
|
7.
|
Нормоконтроль
виконання роботи
|
30.05.11-02.06.11
|
|
|
8.
|
Попередній захист
дипломної роботи
|
03.06.11
|
|
|
9.
|
Остаточне
оформлення роботи
|
04.06.11-05.06.11
|
|
|
10.
|
Отримання відгуку
на роботу
|
06.06.11-10.06.11
|
|
|
11.
|
Рецензування роботи
|
11.06.11-15.06.11
|
|
|
12.
|
Подання роботи до
захисту
|
до 16.06.11
|
|
. Дата видачі завдання «____»_____________ 2011 р.
Керівник: (підпис керівника)
Завдання прийняв до виконання (підпис випускника)
«____»_____________ 2011 р.
NATIONAL
AVIATION UNIVERSITYSystems FacultySystems and Networks Departmentand
Qualifications level: Master of Computer Engineering
: 8.091501 Computer Systems and NetworksBYof the Department
___________ Zhukov I.A.
“____”_____________ 2011Student’s Degree Thesis Assignment
: Domariev Dmytro
1. The Thesis topic: “Information security management system
of a corporate network”by the Rector’s order of “ 15 ” April 2011 № 749
. The Thesis to be completed between 15 April 2011 and 26 June 2011
3. Initial data for the thesis: During the development of the
corporate
network
information security management system concept, act in accordance with the
branch standards of the National bank of Ukraine and the international
standards ISO/IEC. Apply the system approach in efficiency estimation of the
information security management system. Consider the information security
management system as a stochastic system with partial controllability and
observability.
4. The content of the explanatory note (the list of problems
to be considered): Analytical overview of information security management in
corporate networks; Information
security management standards overview; Existent information security
management solutions overview; Mathematical model of information security
system; Definition of the effective system’s features; Improvements provided by
the system; Structure of the system; Interfaces operation and the use of the
main functions.
. The mandatory graphic materials: Deduction hierarchy of
security level estimation; Solutions of the problems in analogous products;
System's database scheme; Excerpt of the information security policy formed by
the system; Program modules of the custom functions (listing).
.
TIMETABLE
|
#
|
Completion
stages of Degree Thesis
|
Stage Completion
Dates
|
Remarks
|
|
1.
|
Scientific-research
internship
|
17.01.11-13.02.11
|
|
|
2.
|
Pre-thesis
internship
|
14.02.11-06.03.11
|
|
|
3.
|
Analysis of the
problem’s current state
|
07.03.11-20.03.11
|
|
|
4.
|
Development of
requirements to the system
|
21.03.11-10.04.11
|
|
|
5.
|
Describing the
proposed system
|
11.04.11-30.04.11
|
|
|
6.
|
Drawing up of
explanatory note
|
01.05.11-29.05.11
|
|
|
7.
|
Standards
inspection
|
30.05.11-02.06.11
|
|
|
8.
|
Preliminary
defence of the thesis
|
03.06.11
|
|
|
9.
|
Final drawing up
of explanatory note
|
04.06.11-05.06.11
|
|
|
10.
|
Supervisor’s
review
|
06.06.11-10.06.11
|
|
|
11.
|
Criticising of
the thesis
|
11.06.11-15.06.11
|
|
|
12.
|
Submission of
thesis to defence
|
before 16.06.11
|
|
. Assignment issue date “____”_____________ 2011.
Supervisor: (signature)accepted for completion (student’s
signature)
Date: “____”_____________ 2011.
Анотація
Домарєв Д.В. Система управління інформаційною безпекою
корпоративної мережі: магістерська робота / Домарєв Дмитро Валерійович,
Національний авіаційний університет, факультет Комп’ютерних систем, кафедра
Комп’ютерних систем та мереж. - Київ 2011. - 114 с., 23 рис., 1 табл., 6
додат., 16 бібліогр.
В роботі застосовано системний підхід до інформаційної
безпеки як універсальну модель процесів інформаційної безпеки. Представлено
математичну модель напів-Марківського процесу для використання в моделюванні
систем захисту інформації. Проведено аналітичний огляд нормативних документів
та існуючих вирішень задля визначення вимог до ефективної системи управління інформаційною
безпекою. Виконане експериментальне впровадження системи в процесі розробки для
випробування запропонованих функцій. Зроблені кількісні оцінки покращень при
застосуванні розробленої системи. Наведено перелік проблем, що розв’язуються
при застосуванні розробленої системи.
В результаті проведених дослідження та розробки, в
пропонованій системі управління інформаційною безпекою системний підхід до
інформаційної безпеки вперше застосовано в управлінні. Інформація в базі даних
системи структурована згідно з системним підходом до інформаційної безпеки.
Уможливлено проведення системного аналізу стану інформаційної безпеки з
багатьох точок зору. Забезпечено створення персоналізованих посадових
інструкцій напряму з первинних нормативних документів.
Наведені рекомендації щодо впровадження та використання
розробленої системи на підприємствах. Практична цінність розробки підтверджена
апробацією.
СИСТЕМА УПРАВЛІННЯ ІНФОРМАЦІЙНОЮ БЕЗПЕКОЮ, СУІБ, МАТРИЦЯ,
СИСТЕМНИЙ ПІДХІД ДО ІНФОРМАЦІЙНОЇ БЕЗПЕКИ, ISO27K, ГСТУ СУІБ
Abstract
Domariev D.V. Information security management system of a
corporate network: master’s degree thesis / Domariev Dmytro, National aviation
university, Computer systems faculty, Computer systems and networks department.
- Kyiv 2011. - 114 pages, 23 figures, 1 table, 6 appendixes, 16 references.the
presented thesis the system approach to information security is applied as a universal model of information
security processes. Mathematical model of semi-Markov process is presented for
the use in information security systems modelling. Analytical overview of legal
documents and existent solutions is performed to define the demands to an
effective information security management system. Experimental implementation
of the system during the development process was performed to test the
introduced functions. Numerical estimations of the improvements due to
developed system application are made. The list of problems solved due to
developed system application is presented.a result of the performed research
and development, in the proposed information security management system the
system approach to information security is applied in management for the first
time. The information in the system’s database is classified according to the
system approach to information security. System analysis of the information
security state from multiple perspectives became possible. Production of
personalised post instructions directly from initial normative documents became
available.are provided for the implementation of the developed system at the
enterprises. The practical value of the product is supported by
approbation.SECURITY MANAGEMENT SYSTEM, ISMS, MATRIX, SYSTEM APPROACH TO
INFORMATION SECURITY, ISO27K, ГСТУ СУІБ
Аннотация
Домарев Д.В. Система управления информационной безопасностью
корпоративной сети: магистерская работа / Домарев Дмитрий Валериевич,
Национальный авиационный университет, факультет Компьютерных систем, кафедра
Компьютерных систем и сетей. - Киев 2011. - 114 с., 23 рис., 1 табл., 6 прил.,
16 библ.
В работе применен системный подход к информационной безопасности в
качестве универсальной модели процессов информационной безопасности.
Представлена математическая модель полумарковского процесса для использования в
моделировании систем защиты информации. Проведен аналитический обзор
нормативных документов и решений с целью определения требований к эффективной
системе управления информационной безопасностью. Выполнено экспериментальное
внедрение системы в процессе разработки для испытания предлагаемых функций.
Сделаны количественные оценки улучшений при применении разработанной системы.
Приведен перечень проблем, решаемых применением разработанной системы.
В результате проведенных исследования и разработки, в предлагаемой
системе управления информационной безопасностью системный подход к
информационной безопасности впервые применен в управлении. Информация в базе
данных системы структурирована согласно системному подходу к информационной
безопасности. Сделано возможным проведение системного анализа состояния
информационной безопасности с различных точек зрения. Обеспеченно создание
личных должностных инструкций напрямую из первичных нормативных документов.
Приведены рекомендации относительно внедрения и использования разработки
на предприятиях. Практическая ценность подтверждена апробацией.
СИСТЕМА УПРАВЛЕНИЯ ИНФОРМАЦИОННОЙ БЕЗОПАСНОСТЬЮ, СУИБ, МАТРИЦА, СИСТЕМНЫЙ
ПОДХОД К ИНФОРМАЦИОННОЙ БЕЗОПАСНОСТИ, ISO27K, ОСТУ СУИБ
Contents
LIST OF TERMS AND ABBREVIATIONS1. INFORMATION SECURITY
MANAGEMENT IN CORPORATE NETWORKS
.1 IS management standards development
.1.1 The ISO/IEC 27000-series
.1.2 The ISO/IEC 27001
.1.3 The ISO/IEC 27002
.1.4 The national peculiarities of the IS management
standards
.2 IS management standards according to the system
approach to IS
.2.1 General position of legal documents in the system
approach
.2.2 The scope of ГСТУ СУІБ 1.0/ISO/IEC 27001:2010
.2.3 The scope of ГСТУ СУІБ 2.0/ISO/IEC 27002:2010
.3 IS management solutions overview
.4 Modern IS management solutions
.4.1 Analytical overview of the existent solutions
.4.2 The most integrated existent IS management
solution
.4.3 Common problems of the existent solutions
.5 Mathematical model of IS
.5.1 General description of the ISS model
.5.2 Semi-Markov process definition
.5.3 ISS state as a semi-Markov process
.5.4 Application of semi-Markov processes in ISS
development
.5.5 Application of semi-Markov processes in ISS state
descriptionto section2. DEFINITION OF THE EFFECTIVE ISMS FEATURES
.1 The mandatory ISMS documents
.2 Content management system for an isms
.3 The information security metrics
.4 Internal audit capabilitiesto section3. INFORMATION
SECURITY MANAGEMENT SYSTEM “MATRIX”
.1 Purpose of the ISMS
.2 General description of the ISMS
.3 Improvements provided by the ISMS
.4 Structure of the ISMS
.4.1 Structure overview
.4.2 Classifying elements
.4.3 Main data storages
.4.4 Program modules
.5 Interfaces of the ISMS
.6 Operation of the ISMS
.6.1 Filling recommendations
.6.2 Reporting
.6.3 Risk assessment
.6.4 Information security policy formationto sectionA.
Deduction hierarchy of ISS security level estimationB. The solutions of the
problems in analogous products by ISMS “Matrix”C. Database schemeD. Excerpt of
the IS policy formed by the productE. Program module of the shared ISMS
functions (listing)F. Program module of the ISMS report (listing)
LIST
OF TERMS AND ABBREVIATIONS
|
EGRC
|
Enterprise
governance, risk and compliance.
|
|
Governance, risk
and compliance (GRC)
|
An integrated
approach adopted by organisations including multiple overlapping and related
activities within these three areas, e.g. internal audit, compliance
programs, enterprise risk management, operational risk and incident
management, etc.
|
|
GRCM
|
Governance, risk
and compliance management.
|
|
Information
security (IS)
|
Preservation of
confidentiality, integrity and availability of information. In addition,
other properties, such as authenticity, accountability, non-repudiation, and
reliability can also be involved [1].
|
|
Information
security control
|
Means of
managing risk, including policies, procedures, guidelines, practices or
organisational structures, which can be administrative, technical,
management, or legal in nature.
|
|
Information
security system (ISS)
|
Aggregate of
security mechanisms that implement the defined rules and satisfy the defined
requirements [2].
|
|
Information
security management system (ISMS)
|
Part of the
overall management system, based on a business risk approach, to establish,
implement, operate, monitor, review, maintain and improve information security
[3].
|
INTRODUCTION
On October 28th 2010, the National bank of Ukraine introduced
the two branch standards in information security management [5]. The documents
[3, 4] are in fact replications of the ISO/IEC 27001 and ISO/IEC 27002
international information security management standards that define the
requirements and rules of development of information security management
systems.regulation 474 of the National bank of Ukraine was passed according to
the article 7 of Law of Ukraine “About the National bank of Ukraine”, article
10 of Law of Ukraine, “About information security in the information
telecommunication systems” and article 10 of Law of Ukraine “About
standardisation”, with the purpose to strengthen the information security in
the Ukrainian banking system [5].addition to mentioned above, the trend of
attraction of foreign investments forces commercial organisations to introduce
international management standards, and information security management
standards in particular.facts explain the rise in demand for the introduction
of international information security management standards in Ukrainian banks
and commercial organisations.methodical instrument described in this work
facilitates the introduction of international standards by providing a methodical
apparatus of optimization of network parameters and structure.
Purpose
and objectives of the investigation
The aim of the presented work is to define and develop the
effective information
security management system (ISMS) for a corporate network.
Investigation object of the presented work is the information security
management in a corporate network.
Investigation subject of the presented work is the ISMS.
Investigation methods used in the research are the following:
1. System approach to IS by V.V. Domarev [2] for
quantitative and qualitative estimation of the IS management efficiency;
2. Semi-Markov processes as the mathematical model of IS processes;
. Analytical overview of the legal documents to form
the general demands to corporate IS management;
. Analytical overview of the existent IS management
solutions to define the effective functions of an ISMS;
. Experimental implementation of the product during
the development process.
Scientific
novelty of the results
The ISMS “Matrix” has the following elements of scientific
novelty.
1. The system approach to IS is applied in management for
the first time.
Before the creation of the product, the system approach to IS
was applied only in theoretical spheres. The examples of such applications are
ISS high-level structure planning and ISS efficiency estimation. These
applications are very important, but most businesses consider them too
expensive in terms of money return. The ISMS “Matrix” applies the system
approach to IS in practical operational management, which is more attractive
for business applications, thus providing higher rates of investments return in
case of deployment at enterprises.
2. The data elements are classified according to the system
approach to IS, which allows uniting knowledge and current tasks in a single
systematised framework.
The sets of values in each of the classifying elements are
formed by the end users for the target organisation or the considered document,
so the obtained system complies both with the system approach to IS and the
business processes of the target organisation, having the structure matching
the system approach and the filling matching the target organisation and
considered documents.
3. System analysis of the IS state can be performed from
multiple perspectives.
The proposed product is intended to facilitate the
introduction of international standards. The final stage of any standard
implementation is certification process, involving wide audit of compliance. It
is known that different inspections analyse the enterprise IS sate from
different perspectives, so theoretically, to pass the audit for several
standards simultaneously, the organisation has to perform several analyses. The
ISMS “Matrix” provides the systematisation of knowledge base (including internal
audit results), thus allowing to present the enterprise IS state from different
perspectives, using same internal audit results for different external checks.
4. Production of personalised post instructions directly
from initial normative documents is available.
To comply with any standard, an organisation must have a
coordinated documentation, that is security policies must conform to corporate
regulation and post instructions must be oriented at enforcing the policies.
The proposed product uses the single systematised knowledge base to generate
the documents, so all the outcomes will be firstly concerted, secondly -
compliant to the target standard, and thirdly - oriented at its implementation.
Practical
significance of the results
The application of the proposed ISMS on state and commercial
enterprises or educational institutions allows to:
1. manage enterprise information security;
2. teach and learn the system approach to IS;
. develop high-level technical task for information
security system creation, considering the system approach and enterprise
peculiarities;
. produce post instructions for international
standards (ISO 27001(2), PCI DSS) implementation.lower price of the proposed ISMS (in comparison to
analogous products present at the Ukrainian market) allows the small and medium
enterprises to save up to 10 times on purchase of an ISMS. Thus, the total
certification cost decreases.of the proposed ISMS provides a possibility to reduce
financial expenses on bringing in external auditors and consultants.
Approbation
of the results
The author presented the practical value of the proposed
product at the xi international conference of young researchers and students
“Polit. Challenges of science today” on April 6-7, 2011.report was awarded the
second place in the section “Mathematics and computer technologies”. The thesis
of the report can be found in [6].
Publications
The author has made publications [7] and [8] concerning the topic of
the presented work before the beginning of the presented research.scientific
value of the results of the performed research and product development is
presented in the publication [9].these publications will be mentioned further in the work in more
detail.
Structure
and volume of the thesis
The presented master’s degree thesis contains introduction,
three sections, conclusions that include the main results of the work,
reference list of 16 items, six appendixes. The full volume of the thesis is
114 pages, including 23 figures and one table.
SECTION 1. INFORMATION
SECURITY MANAGEMENT IN CORPORATE NETWORKS
1.1 IS management standards development
.1.1 The ISO/IEC 27000-series
As the recently accepted information security standards are
strongly based on international ISO/IEC 27000 standards series, the author
considers it necessary to present the information about these
documents.information security standards recently accepted by the National bank
of Ukraine were developed on the basis of ISO/IEC 27000-series standards family
(the so-called “ISMS family”, or “ISO27k” in short).ISO/IEC 27000-series comprises
information security standards published jointly by the International
Organisation for Standardization (ISO) and the International Electrotechnical
Commission (IEC). The standards are the product of ISO/IEC JTC1 (Joint
Technical Committee 1) SC27 (Sub Committee 27), an international body that
meets in person twice a year.series provides best practice recommendations on
information security management, risks and controls within the context of an
overall Information Security Management System (ISMS), similar in design to
management systems for quality assurance (the ISO 9000 series) and
environmental protection (the ISO 14000 series).series is deliberately broad in
scope, covering more than just privacy, confidentiality and IT or technical
security issues. It is applicable to organisations of all shapes and sizes. All
organisations are encouraged to assess their information security risks, then
implement appropriate information security controls according to their needs,
using the guidance and suggestions where relevant. Given the dynamic nature of
information security, the ISMS concept incorporates continuous feedback and
improvement activities, summarized by Deming's "plan-do-check-act"
approach, that seek to address changes in the threats, vulnerabilities or
impacts of information security incidents.first standard of the family, named
ISO/IEC 27000 [1] defines the scope and vocabulary of the whole series.
International Standards for management systems provide a model to follow in
setting up and operating a management system. This model incorporates the
features on which experts in the field have reached a consensus as being the
international state of the art. ISO/IEC JTC 1 SC 27 maintains an expert
committee dedicated to the development of international management systems
standards for information security, otherwise known as the Information Security
Management System (ISMS) family of standards.the use of the ISMS family of
standards, organisations can develop and implement a framework for managing the
security of their information assets and prepare for an independent assessment
of their ISMS applied to the protection of information, such as financial
information, intellectual property, and employee details, or information
entrusted to them by customers or third parties.ISMS family of standards is
intended to assist organisations of all types and sizes to implement and
operate an ISMS. The ISMS family of standards consists of the following International
Standards, under the general title Information technology - Security
techniques.
1.1.2 The ISO/IEC 27001
ISO/IEC 27001 is the formal set of specifications against
which organisations may seek independent certification of their Information
Security Management System (ISMS). The standard specifies requirements for the
establishment, implementation, monitoring and review, maintenance and
improvement of a management system - an overall management and control
framework - for managing an organisation’s information security risks. It does
not mandate specific information security controls but stops at the level of
the management system.standard covers all types of organisations (e.g.
commercial enterprises, government agencies and non-profit organisations) and
all sizes from micro-businesses to huge multinationals. This is clearly a very
wide brief.information security under management control is a prerequisite for
sustainable, directed and continuous improvement. An ISO/IEC 27001 ISMS
therefore incorporates several Plan-Do-Check-Act (PDCA) cycles: for example,
information security controls are not merely specified and implemented as a
one-off activity but are continually reviewed and adjusted to take account of
changes in the security threats, vulnerabilities and impacts of information
security failures, using review and improvement activities specified within the
management system.to JTC1/SC27, the ISO/IEC committee responsible for ISO27k
and related standards, ISO/IEC 27001 is intended to be suitable for several
different types of use, including the following.
1. Use within organisations to formulate security
requirements and objectives;
2. Use within organisations as a way to ensure that
security risks are cost-effectively managed;
. Use within organisations to ensure compliance with
laws and regulations;
. Use within an organisation as a process framework
for the implementation and management of controls to ensure that the specific
security objectives of an organisation are met;
. The definition of new information security
management processes;
. Identification and clarification of existing
information security management processes;
. Use by the management of organisations to determine
the status of information security management activities;
. Use by the internal and external auditors of
organisations to demonstrate the information security policies, directives and
standards adopted by an organisation and determine the degree of compliance
with those policies, directives and standards;
. Use by organisations to provide relevant
information about information security policies, directives, standards and
procedures to trading partners and other organisations that they interact with
for operational or commercial reasons;
. Implementation of a business enabling information
security;
. Use by organisations to provide relevant
information about information security to customers.document [10] provides the
history of the ISO/IEC 27001 development.standard works in the following way.
Most organisations have a number of information security controls. Without an
ISMS however, the controls tend to be somewhat disorganized and disjointed,
having been implemented often as point solutions to specific situations or
simply as a matter of convention. Maturity models typically refer to this stage
as "ad hoc". The security controls in operation typically address
certain aspects of IT or data security, specifically, leaving non-IT
information assets (such as paperwork and proprietary knowledge) less well protected
on the whole. Business continuity planning and physical security, for examples,
may be managed quite independently of IT or information security while Human
Resources practices may make little reference to the need to define and assign
information security roles and responsibilities throughout the
organisation./IEC 27001 imposes the following requirements on the management.
1. Systematically examine the organisation's information
security risks, taking account of the threats, vulnerabilities and impacts;
2. Design and implement a coherent and comprehensive
suite of information security controls and/or other forms of risk treatment
(such as risk avoidance or risk transfer) to address those risks that are
deemed unacceptable;
. Adopt an overarching management process to ensure
that the information security controls continue to meet the organisation's
information security needs on an ongoing basis.
1.1.3 The ISO/IEC 27002
ISO/IEC 27002 is entitled “Information technology - Security
techniques - Code of practice for information security management”. The
standard provides best practice recommendations on information security
management for use by those responsible for initiating, implementing or
maintaining Information Security Management Systems (ISMS). Information security
is defined within the standard in the context of the C-I-A triad: the
preservation of confidentiality (ensuring that information is accessible only
to those authorised to have access), integrity (safeguarding the accuracy and
completeness of information and processing methods) and availability (ensuring
that authorised users have access to information and associated assets when
required)./IEC 27002:2005 has developed from BS7799, published in the
mid-1990's. The British Standard was adopted by ISO/IEC as ISO/IEC 17799:2000,
revised in 2005, and renumbered in 2007 to align with the other ISO/IEC
27000-series standards. The document [11] provides the history of the ISO/IEC
27002 development./IEC 27001 formally defines the mandatory requirements for an
Information Security Management System (ISMS). It uses ISO/IEC 27002 to
indicate suitable information security controls within the ISMS, but since
ISO/IEC 27002 is merely a code of practice/guideline rather than a
certification standard, organisations are free to select and implement other
controls, or indeed adopt alternative complete suites of information security
controls) as they see fit. ISO/IEC 27001 incorporates a summary (little more
that than the section titles in fact) of controls from ISO/IEC 27002 under its
Annex A. In practice, organisations that adopt ISO/IEC 27001 also substantially
adopt ISO/IEC 27002./IEC 27002 is a code of practice - a generic, advisory
document, not truly a standard or formal specification such as ISO/IEC 27001.
It lays out a reasonably well structured set of suggested controls to address
information security risks, covering confidentiality, integrity and
availability aspects. Organisations that adopt ISO/IEC 27002 must assess their
own information security risks and apply suitable controls, using the standard
for guidance. Strictly speaking, none of the controls are mandatory but if an
organisation chooses not to adopt something as common as, say, antivirus
controls, they should certainly be prepared to demonstrate that this decision
was reached through a rational risk management decision process, not just an
oversight, if they anticipate being certified compliant to ISO/IEC
27001.governance, information security is a broad topic with ramifications in
all parts of the modern organisation. Information security, and hence ISO/IEC
27002, is relevant to all types of organisation including commercial
enterprises of all sizes (from one-man-bands up to multinational giants),
not-for-profits, charities, government departments and quasi-autonomous bodies
- in fact any organisation that handles and depends on information. The
specific information security requirements may be different in each case but
the whole point of ISO27k is that there is a lot of common ground.standard is
explicitly concerned with information security, meaning the security of
information assets, and not just IT/systems security. The IT department usually
contains a good proportion of the organisation’s information assets and is
commonly charged with securing them by the information asset owners - the
business managers who are accountable for the assets. However a large
proportion of written and intangible information (e.g. the knowledge and
experience of non-IT workers) is irrelevant to IT.
1.1.4 The national peculiarities of the IS management
standards
As the international standards were introduced in Ukraine by
the National bank and renamed to “branch standards of Ukraine”, certain changes
were made in a standard, predefined by the legal requirements and concrete necessities
of banking industry. Technical divergences and additional information were
attached directly to the sections which they refer to. These attachments are
entitled „National divergence”, „National explanation” or „National remark”.
The “national” insertions primarily explain references to
other international standards, to which the accepted documents refer, or
explain certain terms in more detail than the original standard does. The
standard “ГСТУ СУІБ 2.0/ISO/IEC 27002:2010” also contains national remarks with
recommendations concerning security implementation procedures considering
banking peculiarities.
1.2 IS management standards according to the system
approach to IS
.2.1 General position of legal documents in the
system approach
In 2007, the author conducted a research that formed the
criteria of the classification and the existent normative-legal documents on
providing of information security [7].a result of analysis of normative-legal
documents in the field of providing information security, their classification
was offered. A most essential section at creation of the information security
system of the Ukrainian segment of external communication and data transfer
network of space rocket complex «Cyclone» was remarked. A conclusion was made about
the necessity of concordance of legislative base.creation of the effective
information security system the legislative base, well-organized by the stages
of construction is needed. At the time of the research conduction, providing of
information technologies security is regulated by more than one hundred and
twenty legislative, normative-legal and methodical documents, not coordinated
on terminology, estimation criteria, sequence and directions of creation of the
information security systems.task has been formulated: conduct the analysis of
normative-legal documents in the field of information security technologies.
Classify existent documents with the purpose of concordance of statements of
Ukrainian legislative base.of analysis consisted in the following. The
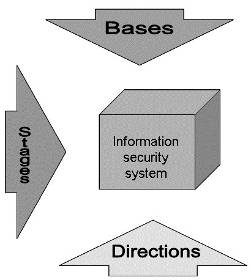
components of information security systems (ISS) can be divided into three
groups, which are illustrated in fig. 1.1:
. Bases (what does ISS consist of);
. Directions (what is intended for);
. Stages (how it works).
 . 1.1. Groups of ISS components
. 1.1. Groups of ISS components
are four bases:
1. Legislative, normative-legal and scientific base;
2. Structure and tasks of subdivisions, providing
security of information technologies;
. Organisationally-technical and regime means (policy
of information security);
. Program-technical methods and tools.are formed
based on the specific features of object to be defended. Taking into account
the typical structure of information systems and historically obtained types of
work on providing information security, it was suggested to consider the
followings directions:
1. Providing security of objects of the information
systems;
2. Providing security of processes, procedures and
programs for information processing;
. Providing security of communication channels;
. Suppression of side electromagnetic radiations.
. Management of the security system.stages of
creation and operation of ISS are the following:
1. Determination of informational and technical resources,
along with objects of the information systems (IS), to be defended;
2. Definition of set of possible threats and
information loss channels;
. Estimation of vulnerability and risks of
information in IS according to present set of threats and loss channels;
. Determination of requirements for information
security system;
. Choosing of means of providing information security
and their specifications;
. Introduction and organisation of the use of the
chosen, methods and means of security;
. Control of the integrity and management of the
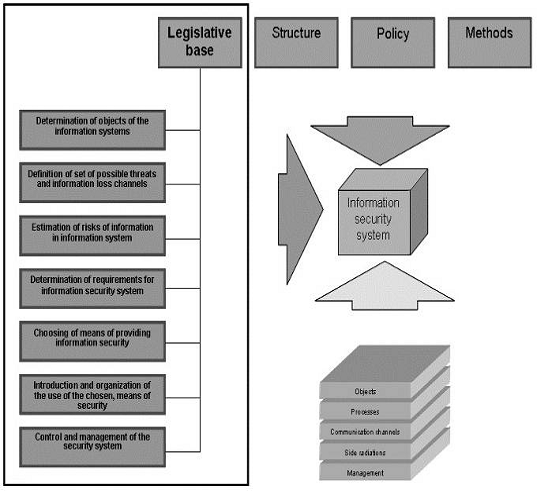
security system.each of directions is related to the bases listed above, in
this report every element of "Legislative … base" is examined with
every element of directions of creation of ISS (see fig. 1.2), namely:
1. Legislative … base of providing security of objects of
the information systems;
2. Legislative … base of providing security of
processes, procedures and programs…;
. Legislative … base of providing security of
communication channels;
. Legislative … base of suppression of side electromagnetic
radiations;
. Legislative … base on a management and control of
the security system.
 . 1.2. The observed segment of ISS
creation
. 1.2. The observed segment of ISS
creation
opened normative documents of the system of technical
information defence of Ukraine have been reviewed. As a result, classification
of legislative documents by the following directions of information security
providing is offered:
. Legislative and conceptual aspects of information
security;
. Organisation information security;
. Protecting information from a loss in technical
channels ;
. Information security in the computer systems;
. Information security in communication and data
transfer networks;
. Suppression of incidental electromagnetic
radiations;
. Cryptographic defence of information;
. Special documents (methods of measuring and
estimation parameters).«Information security in communication and data transfer
networks» was selected as the most essential at creation of the information
security system of the Ukrainian segment of external communication and data
transfer network of space rocket complex «Cyclone». The list of documents in
this section of the offered classification was presented.of normative-legal
documents in remarked direction contained laws, normative documents and
statements of Ukraine on providing of information security.conclusion was made
about the necessity of concordance of terminology and statements of existent
normative-legal documents in area of providing information security with the
purpose of increasing of the Ukrainian legislative base efficiency.conducted
analysis of normative documents allowed to improve the efficiency of providing
information security in the external communication and data transfer network of
space rocket complex «Cyclone».results of the research also formed the
recommendations to the structure of the IS standards that will provide broader
encompassing description of the legislative requirements.to the method
described above, the Ukrainian branch standards in information security management
[3, 4] can be positioned in the framework of the system approach to IS in the
following way.to the system approach to IS by V.V. Domarev described in [2],
the considered object is a document, so it falls in the base “001 Bases” As it
can be observed from the titles of the considered documents, they refer to the
direction “050 - Security system management”. More precise positioning is
determined from the contents of the documents.
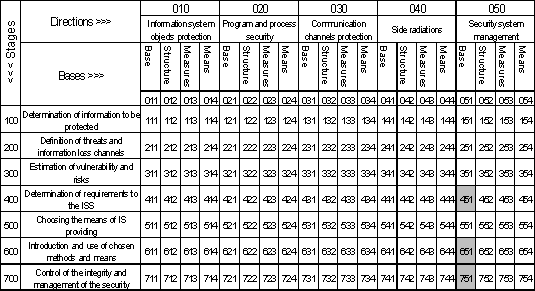
1.2.2 The scope of ГСТУ СУІБ 1.0/ISO/IEC 27001:2010
The section “0.1 General statements” of the introduction to
the document says “This standard is created to supply the model of development,
introduction, functioning, monitoring, revision, maintenance and perfection
information security management system (ISMS)”. Thus the document [3] occupies
the cells 451, 651, 751 which represent normative base of determination of
requirements, introduction and use, control and management in security system
management respectively.final position of the standard [3] in the framework of
the system approach to IS is illustrated by the fig. 1.3. The descriptions of
the cells in the Domarev’s matrix can be found in [2].
 . 1.3. The scope of ГСТУ СУІБ 1.0 in
the system approach matrix
. 1.3. The scope of ГСТУ СУІБ 1.0 in
the system approach matrix
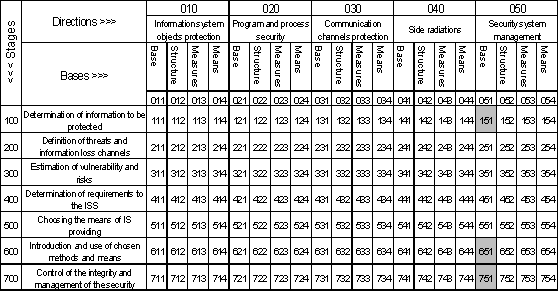
1.2.3 The scope of ГСТУ СУІБ 2.0/ISO/IEC 27002:2010
The section “1 Application sphere” states that the standard
“establishes directives and general principles in relation to establishment,
introduction, support and perfection of information security management in
organisation”. Thus the document [4] primarily occupies the cells 651 and 751
which represent respectively normative base of introduction and use, control
and management in security system management.section “5 Security policy” adds
the cell 151 (normative base of determination of information to be protected in
security system management) to the document’s scope.final position of the
standard [4] in the framework of the system approach to IS is illustrated by
the fig. 1.4. The descriptions of the cells in the Domarev’s matrix can be
found in [2].
 . 1.4. The scope of ГСТУ СУІБ 2.0 in
the system approach matrix
. 1.4. The scope of ГСТУ СУІБ 2.0 in
the system approach matrix
1.3 IS management solutions overview
branch of software related to information security management
named Governance, Risk and Compliance (GRC), appeared in response to the need
of fitting the business security in certain rules. The document [12] provides
the general information about GRC and software solutions in this
area.governance, risk and compliance management (IT GRCM) is maturing as a
technology. The market is growing steadily, but remains relatively small with a
crowded field of vendors. IT GRCM products address requirements to automate
risk management.IT GRCM market comprises vendors that provide software products
to help organisations proactively measure and manage their IT technology and
process controls.IT GRCM market benefits maturing organisations with existing
processes for measuring, managing and reporting IT controls that are ready for
automation.GRCM solutions have a repository; basic document management
capabilities; good workflow, survey and reporting functions; and dashboarding,
with policy content that's specific to IT controls, and support for the
automated measurement and reporting of IT controls.between IT GRCM and
enterprise GRC (EGRC) platforms depends on the focus of the effort. IT GRCM is
recommended for bottom-up, IT-centric requirements, while EGRC platforms are
recommended for top-down enterprise risk management requirements.GRCM
technology continued to mature through 2009 and growth is steady, but the
market remains relatively small ($117 million in 2009) because most
organisations are not ready to implement. IT GRCM automation. The market
continued to grow during the worldwide economic downturn in 2009, indicating
that automating the mapping and measurement of compliance controls remains a
priority for organisations.platforms serve organisations that take an
enterprise approach to compliance and risk management, and that want to have
all business units, including the IT organisation, on the same GRCM solution.
Most vendors with EGRC platforms offer modest IT governance automation
functions. At a minimum, most EGRC vendors offer the capability to document,
survey, and report IT risks and controls, but lack IT-specific content. Some
vendors also provide limited support for an IT asset repository and IT policy
management. Organisations with a primary interest in IT-centric GRCM
requirements should be aware that most EGRC platforms balance finance, operational
and IT requirements at the expense of IT-centric depth.GRCM products support
operation risk management through functions that measure, manage, and report on
IT-centric technology and process controls. Organisations can use IT GRCM
products to document and assess their IT-centric technology and process
controls. The core IT GRCM functions are the following:
. Controls and policy mapping;
. Policy distribution and training attestation;
. IT control self-assessment and measurement;
. IT GRCM asset repository;
. Automated general computer control collection;
. Remediation and exception management;
. Basic compliance reporting;
. IT compliance dashboards;
. IT risk evaluation.software products also help
organisations to proactively measure and manage their IT technology and process
controls. The typical additional functions of these products are the following:
. Definition of IT policies, processes and controls
that are based on best practices;
. Management of policy content;
. Mapping policies to process and technical controls,
as appropriate;
. Automating the measurement of process and technical
controls;
. Evaluating levels of compliance with various
mandates;
. Automating the auditing and regulatory reporting of
these elements.should define their basic approach as top-down or bottom-up, and
use this to guide their requirements definition.top-down approach implies that
IT GRCM is only one of the control categories that will be measured and
reported, along with financial governance and operational requirements such as
environmental, health and safety. Top-down usually requires less-detailed
requirements for gathering general computer control data, such as configuration
and patch data, but places a premium on higher-level reporting to executives. A
top-down approach is more appropriately addressed with EGRC platforms.bottom-up
approach implies greater detail in IT controls for an IT-centric audience. Many
organisations use IT GRCM to organize their vulnerability scan, patch and
configuration control data. Traditional IT GRCM tools are more appropriate for
IT-specific requirements.most significant limiting factor for the IT GRCM and
EGRC products is the divergence of requirements between top-down and bottom-up
approaches. In many cases, organisations are buying two separate tools,
indicating that this difference is more substantial than just vendor marketing
and different buying centres.divergence is based on the differences in management
and reporting requirements for top-down vs. bottom-up. Top-down tends to be led
by enterprise risk management teams addressing business executive requirements,
as opposed to bottom-up requirements, which are typically led by IT or
information security operations teams, The vendors continue to add functions
that overlap top-down and bottom-up requirements, but convergence will only
happen when organisations stop buying multiple tools to address diverging
requirements and agree on one tool as addressing both approaches
comprehensively.comparison of GRC products the following evaluation criteria
are used.understanding - capability of the vendor to understand the buyer and
the major functional requirements of an IT-focused GRC deployment, as opposed
to the requirements of finance or operational-risk-focused GRC deployments.
This criterion is weighed high in general estimation.experience - feedback from
customers that have evaluated or deployed IT GRCM solutions is assessed with
regard to the fit of function to IT GRCM use cases, the maturity and stability
of IT GRCM functions, the code quality, and the quality of support. This
criterion is weighed standard in general estimation.strategy - an evaluation of
the vendor's overall strategy for IT GRCM, including the sales strategy,
product differentiation, capability to capitalize on an existing customer base,
and the use of GRC capabilities to enhance other elements of a technology
portfolio. This criterion is weighed low in general estimation./service - an
evaluation of IT GRCM feature sets as they map to current and future
requirements, with a focus on IT-specific GRC content, IT control assessment
automation, and the capability to assess at IT asset level. This criterion is
weighed high.execution/pricing - an evaluation of the vendor's success in the
market, based on the size and growth rates of the customer base and revenue.
This criterion is weighed low in general estimation.- the capability of the
organisation to meet its goals and commitments in sales, development and
product support. This criterion is weighed low.
1.4 Modern IS management solutions
.4.1 Analytical overview of the existent solutions
The document [12] provides the information for the analysis
of GRC solutions present on the worldwide market as of April 2010. The research
considers products of dominating vendors (Agiliance, BWise, ControlCase, EMC
(RSA), MetricStream, Modulo, OpenPages, Rsam, Symantec, Telos, Trustwave,
Lumension).remains a leader in the IT GRCM market. Although one of the original
vendors to provide an out-of-the-box architecture, Agiliance moved to a modular
offering in late 2009. The highlight of the RiskVision offering remains its
intuitive interface and its top-down approach to managing IT-related controls.
Agiliance continues with a Strong Positive rating in 2010, and should be
considered by organisations that require balanced IT GRCM functionality across
all categories.product’s main strengths are the following.
1. Good out-of-the-box policy and assessment data;
2. The risk assessment functions are comprehensive;
. Good detail and flexibility for confidentiality,
integrity and availability assessments., the product has a problem. It is
concentrated more on assessment, than on managerial functions.is an EGRC
platform. Specific IT GRCM support includes an asset repository, IT-specific
policy and control content, and policy mapping. Although BWise provides a
general computer control integration interface, there's no integration with
specific applications or platforms, BWise has particular strengths for buyers
that are looking for a company-wide approach to GRC rather than an IT-specific
solution, but it will be less appealing to buyers that are specifically focused
on IT security and configuration management controls.product’s main strengths
are the following.
1. Filtering reports to provide targeted views of risks and
controls;
2. Productized rules and connectors;
. Product provides assertion, review and override
workflows that are needed for audit and self-assessment activities., the
product has the following problems.
1. No IT-configuration-level content;
2. No out-of-the-box support for common third-party
general computer control data sources;
. No conditional branching in workflow;
. Limited flexibility in self-assessment compared
with other products in the market.offers IT GRCM as software and as a service,
ControlCase's primary business is Payment Card Industry (PCI) assessment
services, and many of its IT GRCM customers are also using ControlCase
services. The ControlCase GRC framework is composed of nine modules: Compliance
Manager; Vendor Manager; Merchant Manager; Policy Manager; Audit Manager; Asset
and Vulnerability Manager; Incident Manager; Compliance Manager; and Data Discovery,
The product natively collects firewall configuration data and evaluates it
against PCI requirements, which is unique among IT GRCM vendors. There are also
automated sensitive data discovery functions, Self-assessment capabilities are
present, but results analysis is basic. ControlCase is most appropriate for
organisations with PCI-centric IT GRCM requirements and a need for bundled
services.product’s main strengths are the following.
1. Good overall IT GRCM functions;
2. Automated general computer control capabilities are
provided natively through a bundled solution and through integrations with a
few other vulnerability assessment tools., the product has the following
problems.
1. Exception management functions are limited;
2. As a PCI-centric vendor, ControlCase's offerings may
not be appropriate for organisations seeking broader IT GRCM use
cases.(RSA)Technologies (EMC/RSA) offers very good IT GRCM capability, which
also supports a promising EGRC function. Archer was acquired by RSA, the
Security Division of EMC, in 2009. Archer's SrnartSuite Framework provides a
suite that's composed of eight management modules (policy, incident, asset,
threat, risk, vendor, business continuity and compliance) that can be
integrated. It is oriented toward large companies that value the ability to
customize the product to match existing processes. The customizable framework
supports the enablement of additional use cases, which is required for Archer's
expansion into the EGRC market Archer's SmartSuite Framework is sold primarily
as software, but is also provided as a software-as-a-service offering that's
sometimes used as a quick start for new customers.product’s main strengths are
the following.
1. The software offering provides a flexible framework that
can be adapted to resolve a variety of GRC use cases;
2. The ability to customize to fit needs and existing
processes;
. Pending integration with other products in the
EMC/RSA portfolio., the product has the following problems.
1. Cost is frequently raised as an issue by customers and
other evaluators;
2. The Archer Technologies road map may be at risk
after the acquisition - especially the support for providing EGRC platform
functions, due to the IT-centric nature of EMC's core businesses.offers the
EGRC Platform. The company recently introduced the MetricStream IT GRC Solution
to address IT GRCM use cases. Control self-assessment survey, policy
distribution and attestation support is provided. The product provides basic
support for the general computer control use case through out-of-the-box
integrations with BigFix for security configuration assessment, Nessus (through
a third party) for vulnerability assessment, and others through a
user-configurable adapter. Native automated IT assessment capabilities are not
provided. Control management mappings are all based on unified compliance
framework, thereby making MetricStream most appropriate for organisations
seeking a top-down approach to IT GRCM,product’s main strengths are the
following.
1. Good survey functions, including automatically generated
surveys from controls and some out-of-the-box survey content;
2. Native connectors to selected third-party
vulnerability management products;
. Good customer support., the product has a problem.
Content is all based on unified compliance framework that supports the approach
of using single assessment result as a part of different reports, thereby
limiting applicability for bottom-up, IT-centric control management
requirements.is an established IT GRCM vendor with executive management in
Brazil and the U.S., with European operations, and with a growing North
American presence. It has the ability to address EGRC use cases. The company is
large and the products have a good track record, which positions them to do
well in North America. Modulo continued to improve its sales and marketing
presence in North America through 2009. Modulo has a sales office in the U.S.,
but its visibility in competitive evaluations remains limited. IBM Global
Services uses Modulo in its risk assessment consulting engagements. Modulo's
Risk Manager supports the self-assessment, audit support and automated general
computer control use cases. In addition, Risk Manager delivers a large amount
of content for IT technical controls, as well as predefined policy content for
most major security configuration standards. Version 7, which is scheduled to
be released in May 2010, provides a new user interface.product’s main strengths
are the following.
1. Mature products and a strong company;
2. Good auditor workflow support;
. Large amount of vendor-developed content for IT
technical controls, and predefined policy content for most major security
configuration standards;
. Native support for general computer control and
formal support for multiple vulnerability assessment products., the product has
the following problems.
. The maturity of the product has made its interface
complex for users;
. End users have reported configuration
difficulties.is an EGRC product, but it has recently introduced the component
named ITG that provides support for some IT GRCM use cases that are dependent
on unified compliance framework. The majority of OpenPages customers use ITG
for policy management, risk management and compliance reporting. Policy
distribution and attestation functions are flexible and customizable, but the
product currently lacks IT-specific content in this area. The major weakness of
the product is in the area of automated general computer control measurement.
There are no predefined security configuration policies and no native
capability of supported integrations for security configuration assessment or
vulnerability assessment. OpenPages is most appropriate for organisations
taking a top-down approach to GRCM requirements.product’s main strengths are
the following.
1. Use cases that focus primarily on EGRC and secondarily
on IT GRCM;
2. Policy management and self-assessment., the product
has the following problems.
1. Automated collection for general computer control
support is limited to a generic integration interface, and integration with
only one product from third-party vendor is available;
2. Vulnerability assessment support is in development;
. IT-specific content is dependent on unified
compliance framework mappings.Security has rebranded to Rsam to reflect the
evolving usage of its product beyond traditional IT security use cases. The
Rsam product is a strong IT GRCM offering with the ability to support non-IT
requirements. Although Rsam doesn't have its own data collection service, it
supports a third-party application programming interfaces for customers to
execute their own scripts, and supports multiple formats for import from
third-party data collection products. Rsam also supports remediation and
exception management with good workflow, and the risk management function has
the capability to create scoring and correlation among objects, survey
responses and control states. Organisations seeking to automate operational
risk assessment, audit automation and IT control management should consider
Rsam.product’s main strengths are the following.
1. Strong, flexible survey functions with a large amount of
predefined content, and 30 or more predefined surveys;
2. Good workflow to manage the identification and
remediation of threats;
. An application programming interface that customers
have used to integrate with other third-party data collection products;
. Formal integration with 17 commercial scanners;
. Flexible drag-and-drop customization for interface
and reporting., the product has the following problems.
. Rsam lacks a native general computer control
collection capability;
. No predefined security configuration policies.'s
Control Compliance Suite (CCS) is specifically focused on IT GRCM and comprises
three modules: Policy Manager, Standards Manager and Response Assessment
Manager. Automated general computer control is provided by the CCS Standard
Manager, which is widely deployed by customers for configuration policy
compliance in the security operations role. Symantec has the largest installed
base of security configuration policy compliance customers, which is spread
across its CCS Standards Manager and Enterprise Security Manager products.
Symantec is selling Control Compliance Suite into this installed base, and is
beginning to sell it to buying centres that are oriented toward risk and policy
management; however, automated computer control measurement often isn't the
initial focus of these other buying centres. The solution is not optimal for
organisations that want integration with third-party assessment technologies,
because Control Compliance Suite does not provide out-of-the-box integration
with non-Symantec sources. Control Compliance Suite is most appropriate for
Symantec-centric organisations, but not recommended for organisations with
top-down EGRC requirements.product’s main strengths are the following.
2. Largest installed base of general computer control
and measurement users;
. Potential to capitalize on a large service
organisation;
. Symantec has strong native security configuration
assessment capabilities, and also has native network vulnerability assessment
functions., the product has the following problems.
1. Use cases that aren't focused on Symantec technologies
for configuration assessment;
2. Third-party general computer control support is
limited to generic interface - no formal support of specific third-party
sources;
. Symantec integrates with third-party ticketing
systems, but has only basic support for remediation workflow within CCS;
. Mostly compliance reporting with only a light
treatment of risk.provides services and software products primarily to the U.S.
federal government, and is still in the early stages of its expansion into
commercial segments. Telos Xacta IA Manager is primarily oriented to compliance
with government regulations, such as the U.S. Federal Information Security
Management Act (FISMA), automated general computer control measurement, risk
assessment (of technical controls) and tracking mitigation activities. Telos
has expanded Xacta content for common commercial regulations and control
frameworks, but the company still lacks significant experience in servicing
commercial organisations. U.S. federal agencies with FISMA requirements should
put Telos on their shortlists for IT GRCM products.product’s main strengths are
the following.
1. Appropriate for organisations that need to comply with
government regulations;
2. Strong support for automated general computer
control measurement and mitigation workflow;
. Comprehensive asset-oriented technical assessment,
survey evaluation, and reporting. general computer control - strong native
capability in combination with formal integration, with a few major scanners.,
the product has the following problems.
1. Development of policy and control framework content for
commercial regulations;
2. Little support for some aspects of commercial use
cases, such as audit support;
. No policy distribution and attestation function.IT
GRCM capability complements Trustwave's other business units, which specialize
in consulting and PCI compliance. Trustwave GRC has great flexibility through
customization, but little out-of-the-box content. While the product does provide
some out-of-the-box mappings into common regulations and frameworks, there are
gaps for major regulations and control standards. The product lacks a native
automated general computer control collection capability, and it does not
support out-of-the-box integrations with common third-party products to import
configuration and vulnerability data - although there is a general data
integration interface. Trustwave is developing a new technology base for its IT
GRCM offering that will support unified compliance framework. Trustwave will
need to carry both products and define a migration path to the new
technology.product’s main strengths are the following.
1. Product is a good fit for organisations that are looking
for a flexibility, and that wish to have consultants customize and configure
their IT GRCM functions;
2. Surveys, workflow and policy attestation support
control self-assessment., the product has the following problems.
1. Although Trustwave GRC supports drag-and-drop
associations between controls and control objectives, it doesn't provide
out-of-the-box mappings into common regulations and frameworks;
2. The product doesn't provide native general computer
control collection, nor does it support out-of-the-box integrations with common
third-party products to import configuration and vulnerability data (although
it can be customized to do so);
. Trustwave will be moving to a new technology base -
and it will need to carry both products and define a migration path to the new
technology.
1.4.2 The most integrated existent IS management
solution
Information security management products presently offered on
the Ukrainian market include mostly the narrow solutions: risk managers,
compliance scanners and penetration tests (network perimeter tests).most
integrated IS management solution present in the Ukrainian market today is
“Lumension Endpoint Management and Security Suite” (L.E.M.S.S.) produced by
Lumension Security, Inc., a worldwide leader in operational security. The
company became famous due to its developments, integrations and marketing of
endpoint security software solutions that help businesses protect their
critical information and manage the most important risks in the computer
network assets.product itself is a composition of five special-purpose
sections: vulnerability management, endpoint protection, data protection,
compliance and it risk management, endpoint operations. The fig. 1.5 below is a
generalised scheme of the product’s structure from the official datasheet [13].
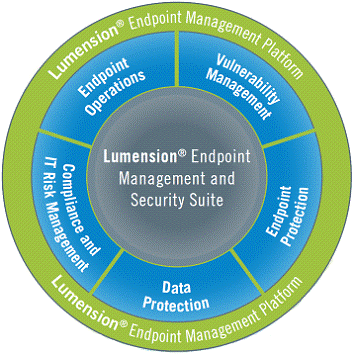 . 1.5. The official illustration of
the Lumension Endpoint Management and Security Suite structure
. 1.5. The official illustration of
the Lumension Endpoint Management and Security Suite structure
of the sections are subdivided into product modules. Endpoint
Operations Product Modules are Patch and Remediation, Security Configuration
Management, Enterprise Reporting. Endpoint Security and IT Risk Management
Product Modules are Application Control, AntiVirus, Device Control, Risk
Manager. The structure is described more in detail below.
1. Endpoint operations product modules
1.1. Patch and Remediation: Reduces corporate risk and
optimizes IT operations through the timely, proactive elimination of operating
system and application vulnerabilities across all endpoints and servers.
1.2. Security Configuration Management: Ensures that
endpoints are securely configured and in compliance with industry best
practices and regulatory mandates.
.3. Enterprise Reporting: Provides centralized
visibility of IT assets and consolidates vulnerability and configuration data
across the enterprise.
2. Endpoint security and it risk management product modules
2.1. Application Control: Enables the enforcement of
application usage policies to ensure that only software that is explicitly
authorized or trusted is allowed to execute.
2.2. AntiVirus: Provides comprehensive protection against
all malware including viruses, spyware, Trojans and adware.
.3. Device Control: Identifies all removable devices
that are now or have ever been connected to your endpoints and enforces device
/ port access and data encryption policies to prevent data loss and/or theft.
.4. Risk Manager: Automates compliance and IT risk
management workflows and provides necessary visibility of people, processes and
technology across the entire organisation. Imports scan data from multiple
Lumension products and 3rd party scanning devices to its standalone
interface..E.M.S.S. is positioned as a solution that will provide an extended
control over the corporate workstations, at the same time reducing the control
complexity by centralising the management functions and automating the network
data mining.’s rapidly changing IT network is more distributed and virtual than
ever sensitive data is often stored on remote endpoints, such as laptops and
mobile PDAs, and accessed through public Wi-Fi networks connected to an
organisation’s IT network via the Internet. Mounting budget pressures are
forcing companies to look increasingly at virtual and cloud-based computing
alternatives. In addition, traditional point-based technologies and solutions
have added more complexity and cost to organisations, because IT teams are
focusing on the integration of disparate technologies and have to use many
different consoles across multiple products.IT environments have become
increasingly dynamic and distributed with data flowing across a myriad of
devices and platforms, companies have effectively lost control of their
information.approaches and solutions are required to ensure enhanced security
and compliance with the lowest total cost of ownership possible. The once-separate
IT functions of operations and security must collaborate and share information
seamlessly to proactively address IT risk in a more effective and efficient
manner. Lumension Endpoint Management and Security Suite is an extensible
solution suite developed on the Lumension Endpoint Management Platform that
reduces management complexity, minimizes TCO, improves visibility and delivers
information control back to IT..E.M.S.S. is intended to provide the following:
1. Reduced complexity and TCO via an agile infrastructure,
which delivers modularly licensed product capabilities through an integrated
console and single-agent architecture;
2. Greater visibility and control with an end-to-end
approach that includes capabilities to meet endpoint operations, security,
compliance and IT risk management needs;
. Enhanced security, reduced operational friction and
greater control of endpoints via Lumension Intelligent Whitelisting, which
combines Lumension AntiVirus, Lumension Application Control, and Lumension Patch
and Remediation with a trusted change management engine into a unified
workflow;
. Endpoint power management which reduces power
consumption costs and enables the management and security of both online and
offline endpoints.key benefits of the product are stated to be the following:
1. Reduce it environment complexity;
2. Decrease endpoint total cost of ownership;
. Provide greater visibility into and control over
customer’s network’s endpoints;
. Raise security and compliance posture;
. Support customer’s it operational and security
mandates within a dynamic business environment;
. Rationalize endpoint management and security
workflows;
. Ensure continuous endpoint protection.features of
the product are stated as the following
1. Integrated endpoint management console: Web-based
console and workflow-based navigation simplify and optimize IT operations.
2. Modularly licensed capabilities: An extensible
platform that enables both Lumension capabilities as well as 3rd party
developed capabilities to be easily integrated.
. Comprehensive and automated reporting: Delivers a
holistic view of your environmental risk with a full range of operational and
management reports that consolidate information within a single management
console.
. Continuous and full discovery of the it
Environment: Integrates award-winning solution capabilities to provide complete
discovery of what’s in your IT environment, including capabilities such as
application whitelisting, device control, patch management, anti-virus and
configuration management.
. Scalable and agile architecture: Delivers both pull
and push approaches to endpoint communication and policy distribution.
. Optimized compliance and it risk management:
Streamlines compliance and IT risk management workflows and ensures continuous
monitoring of compliance and IT risk postures.
. Power management policy enforcement: Centralizes
power management policies to achieve maximum energy efficiency for both online
and offline machines. Wake- On-LAN capability ensures that offline machines
receive critical patches and software updates.
. Single promotable agent: Flexible agent
architecture delivers services on the fly without requiring burdensome upgrades
or agent bloat, provides easy agent install / uninstall capabilities, and
offers self-monitoring and recovery capabilities., L.E.M.S.S. lacks top-level
management instruments that would provide understandable control interface for
anyone from the board of directors, independently on profession.
1.4.3 Common problems of the existent solutions
Of existent solutions on the Ukrainian market, none covers
all the aspects (requirements) of the standards.the most integrated IS
management solution present on the Ukrainian market today, uniting the narrow
functional modules into a broader security coverage, lacks certain features
that would make it an effective management tool.
.5 Mathematical model of IS
.5.1 General description of the ISS model
The author conducted the research [8] on the mathematical
models of IS. The state of the information systems and information security
systems was modelled as a semi-Markov process. Application of semi-Markov
processes in development of the ISS was classified through the matrix of
connections of elements. A conclusion was made about applicability of models,
based on semi-Markov processes, in development and state description of the ISS
for the increase of exactness of their efficiency estimation.of intense
development and wide distribution of IT, the development of the ISS became important
part of the information systems creation process. At the time of the research a
problem of combating the newest threats (the so-called "zero-day
attacks"). For the increase of the modelling efficiency in design of
functioning and attack reactions of the information systems, the Semi-Markov
processes can be applied.information security system (ISS) is a complex of
legislative, organisational, technical and other measures and tools, providing
the protection of important information from threats and loss channels in
accordance with the stated requirements.has a special purpose which at
formalised level acquires multidimensional character. The multidimensional
(integral) task of information security requires the implementation of the
system approach including the modelling of defence processes based on
scientific methods.specific features of the solution for such a task are the
following.
1. Presence of multiple criterions, related to the
necessity of account of large number of individual indexes (requirements);
2. Incompleteness and vagueness of initial information;
. Impossibility to apply the classic optimization
methods;
. Necessity of obtaining both qualitative and
quantitative indexes of the information security system efficiency.system
approach to information security is a way of thinking and analysis, in
obedience to which the security system is examined as an aggregate of associate
elements, having a common goal - to provide the information security. In case
of purposeful interconnection of elements, ISS acquires specific properties,
initially inherent to none of its components. Thus those properties of
elements, which determine the degree of their co-operation and influence the
system as a whole, have a primary value.a methodical point of view, determination
of ISS efficiency consists in measuring the proper indexes and producing
judgement about the accordance of certain methods and tools of defence to the
set requirements and the purpose of ISS., the process of ISS creation is
implied by establishing hard logical and functional connections between the
heterogeneous security elements. Thus, the importance of properties of separate
ISS elements decreases, and general system tasks are pulled out on the first
plan. As practice shows, it is the quality of stated connections determines the
efficiency of the security system as a whole.increase the ISS efficiency, it is
possible to use the system approach to IS offered by V.V. Domariev in [2]. The
approach determines the interconnections between concepts, definitions,
principles, methods and mechanisms of security. The system approach is
applicable not only in ISS development, but also on all the stages of the
information systems life cycle. Thus all the tools, methods and measures, being
in use for maintaining security are united into a single mechanism.of IS, used
in the system approach is separated on three groups of elements: bases (what
consists of), directions (what is intended for), stages (how works). The
relations between the components are presented as a matrix of knowledge
(presented in fig. 1.6), where the contents of every element describes the
interconnection of constituents.
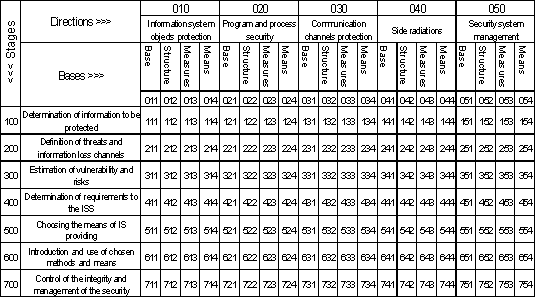
Fig. 1.6. The numeration of elements in the Matrix of
knowledge
1.5.2 Semi-Markov process definition
The work [14] is devoted to the mathematical description of
semi-Markov process. A semi-Markov process is a Markovian process with random
transition intervals, thus being Markovian only at the transition instants.
Describing a semi-Markov process with N states, it is needed to specify N2
transition probabilities pij determining the transition to state j, if the
present state is i, satisfying the conditions (1.1).
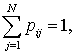 i
= 1,2,...,N; pij ≥ 0, 1 ≤ i, j ≤ N.(1.1)
i
= 1,2,...,N; pij ≥ 0, 1 ≤ i, j ≤ N.(1.1)
time interval between the transitions is determined by random
variable τij, governed by a corresponding set
of N2 holding-time density functions (1.2).
(·), 1 ≤ i, j ≤ N.(1.2)
Thus, it is convenient to define a semi-Markov process by transition
probability and holding-time density functions matrices of size N´N, respectively P={pij} and
H(·)={hij(·)}.a process enters a state, the next state and holding time are
determined by transition probabilities and holding-time density functions.
After holding in state i for the time τij, the process makes the
transition to state j and repeats the whole procedure.
Let the current state be ξ(t). Taking into account
that the modelling is applied to ISS, transitions of the system to the same
state would not be considered (pii=0). The chart of a semi-Markov process is
presented in fig. 1.7, a.ccW(t)={ccwi(t)} be the diagonal matrix of probabilities that
the system will not leave the state i until after time t.matrix flow graph
representing semi-Markovian transitions is presented on fig. 1.7, b.
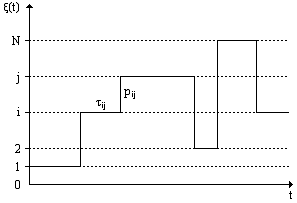
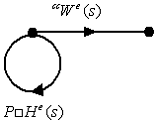 b.
1.7. Semi-Markov
process chart and its matrix flow graph
b.
1.7. Semi-Markov
process chart and its matrix flow graph
, semi-Markov process is described by the interval-transition probability matrix
(1.3).
Φe(s)=[I-P□He(s)]-1
ccWe(s),(1.3)
where I - unit matrix, □ - element by element matrix
multiplication, e(s) - the exponential (Laplace) transform matrix (1.4).
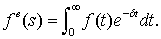 (1.4)
(1.4)
1.5.3 ISS state as a semi-Markov process
The state of an information system as well as an ISS can be
described as a continuous-time semi-Markov process that has an arbitrary
transition probability matrix and all holding times given by an exponential
distribution (1.5).
(t) = λe-λt, 1 ≤ i, j ≤
N.(1.5)
Then the interval-transition probability matrix will be
described by the formula (1.6).
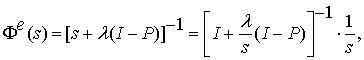 (1.6)
(1.6)
the state graph will have either of the two forms shown in
fig. 1.8.
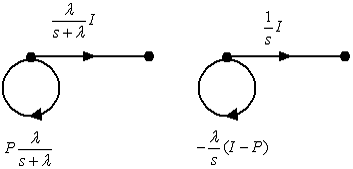 b.
1.8. Matrix flow graphs of the continuous time semi-Markov process
b.
1.8. Matrix flow graphs of the continuous time semi-Markov process
The foregoing description of the information system state can
be accepted as a basis of its generalised functioning model. The basic purpose
of generalised models consists in creating the pre-conditions for the objective
estimation of the general information system state from the view of either
vulnerability measure or information protection level. A necessity for such
estimations usually arises at the analysis of general situation with the
purpose of making strategic decisions during organisation of information
security. The general models of the systems and information security processes
are ones that allow to determine (to estimate) the general characteristics of
the considered systems and processes, unlike local and private models, which
provide determination (estimation) of some local or private descriptions of
systems or processes.short list and descriptions of models, in which the
Semi-Markov processes can be applied, is presented below.model of information
security process. This model, in the most general view and for the most general
object being protected, must display the information security process as a
process of co-operation of random destabilising factors, affecting information,
and information security tools that hinder the action of these factors. The
result of co-operation will be a certain level of information security;model of
the ISS. Being further development of general information security process
model, the generalised model of the ISS must display the basic procedures,
carried out inside this system with the purpose of rationalisation of
information security processes. These processes in the most general view can be
presented as distribution and use of information security resources as
reactions on random changes in influence of destabilising factors;of general
estimation of information threats. The basic purpose of this model is
estimating not simply the information threats, but also those losses which can
take place as results of different threats. The models of this direction are
also important because exactly in them those conditions, at which estimations
can be adequate to the real information security processes, are exposed in the
most degree;of analysis of the systems that differentiate access to the
information system resources. The models of this class are intended to support
the decision of tasks of analysis and synthesis of the systems (mechanisms)
that differentiate access to the different types of information system
resources and foremost to the data arrays. The separation of these models into
an independent class of general models is supported by the fact that that the
mechanisms of access differentiation belong to the most substantial components
of the ISS, and the general efficiency of information security in information
system depends no the efficiency of access differentiation to a great extent.
In these models the Semi-Markov process can illustrate the access to the
information with the different degree of secrecy, where the states will be
authentications on the different security levels.
1.5.4 Application of semi-Markov processes in ISS
development
Planning, organisation and application of ISS are actually
related to the unknown events in the future and always contain the elements of
vagueness. In addition, other sources of ambiguousness are present, such as
incomplete information for making administrative decisions or
social-psychological factors. Therefore, it is natural that considerable
vagueness accompanies the stage of ISS planning. The ambiguousness level can be
lowered by application of the most adequate models.Semi-Markov processes can be
applied in ISS development as a universal tool of information systems
functioning modelling on the stages of possible threats and information loss
channels, and estimation of vulnerability and risks. The Semi-Markov processes
application domain corresponds to elements 204 and 304 (fig. 1.9). A zero in
the second digit means coverage of all the directions. Thus, the Semi-Markov
processes are included in means that perform the following tasks.
1. Provide efficiency and quality in definition of set of
possible threats and information loss channels on objects in information
system, in processes and applications of information system, at an information
transfer along communication channels, due to side electromagnetic radiations,
and also in the process of security system management;
2. Determine the conduction of estimation of
vulnerability and risks of information on objects in information system, in
processes and applications of information system, at an information transfer
along communication channels, due to side electromagnetic radiations, and also
in the process of security system management.
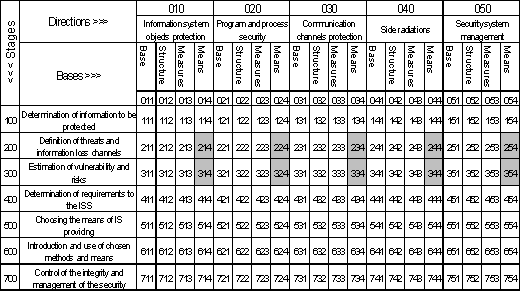 . 1.9. The scope of semi-Markov
processes application in the Matrix of knowledge
. 1.9. The scope of semi-Markov
processes application in the Matrix of knowledge
1.5.5 Application of semi-Markov processes in ISS
state description
According to the modern theory of systems efficiency
estimation, ISS quality shows up only in the process of its use on purpose
(special purpose functioning), therefore an evaluation on the efficiency of
application is the most objective.a basis of complex of indexes and criteria of
ISS efficiency estimation, probability of the objective fulfilment by the
system (providing the required security level) must be used. Thus the concepts
of suitability and optimality serve as criteria of estimation. Suitability
means implementation of all the requirements set to ISS, and optimality is
achievement by one of characteristics its extreme value at the observance of
limitations and conditions applied to other properties of the system.describe
the ISS state, it is enough to make the Matrix of estimations (an example is
presented in fig. 1.10), containing in its cells the estimations of efficiency
of the proper system elements. In case of change in any information system
parameter one or more Matrix of estimations elements may change due to logical
connections. That influences the generalised indexes. Consequently, the general
ISS state changes. The logical deduction hierarchy of ISS security level estimation
is presented in Appendix A.
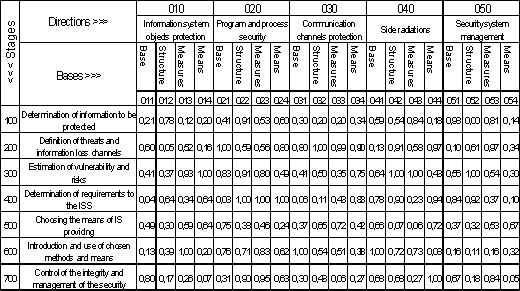 . 1.10. Matrix of estimations
. 1.10. Matrix of estimations
into account the character of these changes, it is possible
to suppose that the functioning of ISS is also a Semi-Markov process. This
conclusion allows describing the changes of the ISS state through relatively
simple mathematical model. Mathematical models of information system
functioning based on the Semi-Markov processes can be used in simulation of
attacks on information system, which will promote the efficiency of threats
counteraction measures development.conclusion can be made that the semi-Markov
processes can be applied in design and state description of the ISS. The models
of the information systems activity based on semi-Markov processes can be used
to increase the accuracy of the ISS efficiency estimation, as well as in ISS
development.
Conclusions to section
development of the IS management standards was presented.main
modern international IS management standards were described.national
peculiarities of the IS management standards were highlighted.IS management
standards were positioned according to the system approach to information
security. The places of the national IS management standards in the system
approach framework were illustrated.existent IS management solutions were
overviewed and the most integrated existent IS management solution was
highlighted. The major strengths and problems of the existent IS management
solutions were stated.Markov processes were suggested as a mathematical model
of IS.the current state, problems and demands of the information security
management branch, the author concludes that an ISMS with analytical potential
is needed to satisfy the requirements of the branch, as well as to rise the
sufficiency of the IS management in organisations. The analytical functions of
the product should facilitate the IS audit and management in the target
organisation.maintenance can be considered as a stochastic system with partial
observability and controllability. These properties must be accounted in the
development of an ISMS.features needed in an effective ISMS are defined in the
section 2.
SECTION
2. DEFINITION OF THE
EFFECTIVE ISMS FEATURES
2.1 The mandatory ISMS documents
branch standards of Ukraine “ГСТУ СУІБ 1.0/ISO/IEC
27001:2010” [3] and “ГСТУ СУІБ 2.0/ISO/IEC 27002:2010” [4], imply certain
requirements to an ISMS. The document [15] describes the main of these
requirements.begin with, the ISMS must operate based on certain policies.
Otherwise, such policies may be produced in the process of its development or
functioning. The work [16] proposes the following mandatory ISMS documents.of
key management decisions regarding the ISMS, for example, minutes of management
meetings, investment decisions, mandating of policies, reports etc., not
individually specified in the standard apart from the following specific
items.security policy set matches the characteristics of the business, the
organisation, its location, information assets and technology, including an
ISMS policy and information security policy.ISMS policy defines the
objective-setting management framework for the ISMS, giving it an overall sense
of direction/purpose and defining key principles. The ISMS policy must possess
the following properties:
1. Take account of information security compliance
obligations defined in laws, regulations and contracts;
2. Align with the organisation’s strategic approach to
risk management in general;
. Establish information security risk evaluation
criteria;
. Be approved by management;security policy or
policies specifies particular information security control objectives or
requirements in one or more documents. This document should also be approved by
management to have full effect.scope defines the boundaries of the ISMS in
relation to the characteristics of the business, the organisation, its
location, information assets and technology. Any exclusions from the ISMS scope
must be explicitly justified.security procedures, that are written descriptions
of information security processes and activities, for example, procedures for
user ID provisioning and password changes, security testing of application
systems, information security incident management response etc.documentation,
for example, technical security standards, security architectures/designs etc.
and referencing ISO/IEC 27002 (details vary between ISMSs).assessment methods,
which are policies, procedures and/or standards describing how information
security risks are assessed.assessment reports document the results, outcomes,
recommendations of information security risk assessments using the methods
noted above. For identified risks to information assets, possible treatments
are applying appropriate controls, knowing and objectively accepting the risks
(if they fall within the information security risk evaluation criteria),
avoiding them; or transferring them to third parties. The information security
control objectives and controls should be identified in these reports.treatment
plan, which is a project plan describing how the identified information
security control objectives are to be satisfied, with notes on funding, roles
and responsibilities.operating procedures, that are written descriptions of the
management processes and activities necessary to plan, operate and control the
ISMS, for example, policy review and approvals process, continuous ISMS
improvement process.security metrics describes how the effectiveness of the
ISMS as a whole, plus key information security controls where relevant, are
measured, analyzed, presented to management and ultimately used to drive ISMS
improvements.of Applicability states the information security control
objectives and controls that are relevant and applicable to the ISMS, generally
a consolidated summary of the results of the risk assessments, cross-referenced
to the control objectives from ISO/IEC 27002 that are in scope.control
procedure explains how ISMS documents are approved for use, reviewed, updated,
re-approved as necessary, version managed, disseminated as necessary, marked
etc.control procedure explains how records proving conformity to ISMS
requirements and the effective operation of the ISMS (as described elsewhere in
the standard) are protected against unauthorized changes or destruction. Again,
this procedure may be copied from the QMS or other management
systems.awareness, training and education records document the involvement of
all personnel having ISMS responsibilities in appropriate activities (for
example, security awareness programs and security training courses such as new
employee security induction/orientation classes). While not directly stated,
the requirement for information security awareness materials, training
evaluation/feedback reports etc. may be inferred.ISMS audit plans and
procedures state the auditors’ responsibilities in relation to auditing the
ISMS, the audit criteria, scope, frequency and methods. While not stated
directly, ISMS audit reports, agreed action plans and
follow-up/verification/closure reports should be retained and made available to
the certification auditors on request.action procedure documents the way in
which nonconformities which exist are identified, root-causes are analyzed and
evaluated, suitable corrective actions are carried out and the results thereof
are reviewed.action procedure, which is similar to the corrective action
procedure but focuses more on preventing the occurrence of nonconformities in
the first place, with such activities being prioritized on the basis of the
assessed risk of such nonconformities.
2.2 Content management system for an isms
ISMS may rely on a content management system to support the
exchange of information, for example, audit reports, policies, etc. The content
management system must be selected knowing specific requirements of the enterprise.
It is recommended to consider a structured specification and evaluation process
such as that for choosing risk analysis/management methods.exist free or open
source and commercial products designed to support ISMSs and ISO27k. Their
types are Content Management Systems (CMS), Document Management Systems (DMS),
Learning Management Systems (LMS) and Policy Management System (PMS).a system
is nevertheless optional, and information exchange can be directly supported by
an ISMS or be performed manually for relatively small businesses or at higher
managerial levels.
2.3 The information security metrics
quality of the IS can be measured through various parameters,
ranging from number of blocked spam messages to the degree of attaining a
strategic goals. As for an ISMS, the author strongly insists on measuring the
effectiveness by managerial indexes, such as number of completed low-level
tasks, the conventional risk value, eliminated by a security measure, etc. Such
evaluation yields better understanding at high executive levels.
2.4 Internal audit capabilities
second ultimate goal of implementing an ISMS, except
providing a comprehensive IS management for the enterprise, is the
certification of accordance to one or several of the ISO27k standards.certification
process assumes the external audit of the corporate ISS to define the
compliance with the standard. To guarantee the successful external audit, a
company may induce internal security audits preliminary to certification.the
ISMS contains and manipulates the most important security assessment data, the
introduction of audit functions may seriously facilitate the internal audit
procedures.
Conclusions to section
management standard development national
Taking into consideration the stated problems and
requirements to an ISMS, the following features and functional capabilities are
needed in an information security management product.
1. High-level managerial presentation by the introduction
of simple interfaces and reports oriented specifically at the high-level
management;
2. Monitoring and management of the IS risks at the
enterprise with immediate reassessment in case of any changes in the sets of
assets and threats;
. Planning of external or internal IS audit, control
of the audit procedures progress by pivot reports;
. Registration of violations, deviations and remarks
in the process of audit procedures fulfilment by supplying the needed
information in a specialised report;
. Use of templates for policies, descriptions and
other working documents. These templates must comply with the national
standards;
. Creation and keeping all the necessary dispositive
and regulation documents on IS (functional duties, instructions, security
policies, etc.) by storing, updating and supplying the corporate IS information
to the documents directly;
. Maintaining the common databases of knowledge and
methodical materials, archiving to supply management decisions with actual
data;
. The conduction of analysis of the IS state (matrix
of the state) and forming of management-level reports as comprehensible tables
and charts, as it is usually hard to deliver the IS issues to unfamiliar
people;
. Rational distribution of the roles and plenary
powers, allocation of resources to officials and tasks;
. Informative-analytical support of decisions by
organisation’s management as to the process of IS management, because having
clear and actual information, it is easier to take rational decisions;
. Providing the forming of requirements (matrix of
requirements) and ISMS efficiency estimation indexes (matrix of estimations),
which is important in controlling the achievement of the set objectives;
. Estimation and management of the budget of the ISMS
creation and exploitation, to control the expenditures on the ISMS in
particular, or the overall organisation’s IS;
. Monitoring of tasks execution and rendering of
recommendations to boost the overall performance for the projects.
SECTION
3. INFORMATION SECURITY
MANAGEMENT SYSTEM “MATRIX”
3.1 Purpose of the ISMS
basic task of the ISMS is the informative-analytical support
of the process of the ISS creation attributable to the precise estimation of
the accepted decisions efficiency, and choice of the rational hardware,
software and organisational solutions.“Matrix” is based on system approach to
information security by Domarev V.V. as well as on universal experience of
different companies.proposed ISMS provides the following functional
capabilities:
1. Development of documentation;
2. Personnel management;
. Rational choice of software and hardware IS means
and solutions;
. Forming the terms of reference and projects
management;
. Management of information assets and resources;
. Analysis of threats;
. Estimation of risks;
. Planning, development and implementation of
organisational and technical measures of IS;
. Estimation of the IS efficiency;
. Accumulation of informative-analytical knowledge
and experience;
11. Training and education of organisation’s specialists
in information security.
3.2 General description of the ISMS
The “Matrix” is positioned as an information security management,
international IT standard implementation and decision support system. The ISMS is an
information-methodological instrument of IS management, which is the simple,
versatile and effective mean of creation, management, control and estimation of
the efficiency of the IS providing processes in organisations.“Matrix” is a
systematic decision that is intended to organize the cooperation of the organisation’s
management, IT department, IS service, specialists of internal audit and other
departments in the process of IS management in the organisation.ISMS “Matrix”
is projected for organisation of information security management processes in
accordance with the requirements of standards of the National bank of Ukraine
or other normative documents. The system also allows to independently organize
the work for the creation of the ISS and easily adapts itself for the solution
of concrete IS providing tasks with taking the business processes peculiarities
into consideration.of the ISMS “Matrix” provides a possibility to reduce
financial expenses on bringing in external auditors and consultants.ISMS
“Matrix” is based on the principles of the system approach to IS management,
absorbing the knowledge and the best practices of the leading companies that
provide IS. The
system
consists of database, containing the sets of operational tasks and knowledge.
Each element of these sets is classified by Domarev’s Matrix (element is
assigned to a stage, a direction and a base). This allows systematising and
uniting IS management and knowledge.
3.3 Improvements provided by the ISMS
application allows to:
1. increase the efficiency of
management decisions;
2. systematise and unite the
forces of different specialists for the achievement of common goal
(implementation of one or several international IS standards simultaneously);
3. estimate the current state
of ISS and its compliance to a certain IS standard;
4. obtain pivot reports on
ISS state, current and finished jobs (in extension, updating, etc.)to the
research of the analogous products presented in [12], there exist certain
problems in IT GRCM software. The explanations of the solutions and their
effects are presented below.following improvements became possible due to the application of the
developed ISMS “Matrix”.situation when the product is concentrated more on
assessment, than on managerial functions is resolved because the main function
of the developed ISMS is high-level management. Thus the managerial efficiency
of the product increased.problem of absence of the conditional branching in
workflow algorithms is eliminated because the developed ISMS supports workflow
that is not limited to business processes with strict algorithms. Thus the
developed ISMS can be applied to the non-trivial business
situations.flexibility in self-assessment is resolved because the operation of
the developed ISMS is based on self-assessment data and is dynamically rebuilt
in reply to any changes in the structure, operation or normative provision of
the target organisation. Thus the developed ISMS extends the self-assessment
abilities of the target organisation.when products may be concentrated on a
single standard and not appropriate for broader use is resolved because the
system approach to IS enables handling of any normative documents - from
internal regulations to international standards. Thus the developed ISMS can be
used to implement wider scope of standards.price of the developed ISMS for the
customers is considerably lower than for analogous products because the system
core is distributed freely and support pricing is low due to immaturity of the
product. Thus the developed ISMS is more affordable than analogous
products.situation when content is all based on bottom-up, IT-centric control
management requirements is resolved because the developed ISMS is designed to
operate only on high managerial levels, preventing from drowning in the vast
amount of technical details. Thus overall clearance of the IS state at the
target organisation is maintained.situation when maturity of the products makes
their interfaces complex for users is resolved because the interfaces if the
developed ISMS can be adapted on demand for each customer. Thus the developed
ISMS is more convenient for the end users.configuration difficulties for the
end users are eliminated because no end-user configuration is needed, except
allowing MS VBA macros. Thus the developed ISMS has faster deployment.absence
of predefined security policies is compensated by the availability of filling
the developed ISMS according to any normative document or policy from product
support unit. Thus the developed ISMS has the improved adaptability to the
defined IS policy or other normative documents.presence of mostly compliance
reporting with only a light treatment of risk is resolved in the developed ISMS
because risk assessment is a dedicated function, providing both detailed risk
estimations and pivot charts. Thus the balance between the treatments of
compliance and risks is established in the developed ISMS.hardships in
development of policy and control framework content for commercial regulations
were eliminated because the system approach to IS used in the developed ISMS is
equally effective in both state and commercial organisations. Thus the
developed ISMS obtained wider application scope in terms of target organisation
spheres.limited audit support is resolved in the developed ISMS by the presence
of the variety of reports and pivot charts that allow to pass various audits
without reassessment. Thus the developed ISMS shortens the preparation time
before multiple audits conduction.appendix B generalises the problems solved in
the developed ISMS “Matrix”.of the developed ISMS also has financial
advantages. The following numerical estimations were made.
1. The price of the product and technical support is 10
times lower in average.
2. The cost of training internal auditors (ranging from
about 5000 to 8000 UAH) is compensated by the inherent audit capabilities of
the ISMS “Matrix”.
3.4 Structure of the ISMS
.4.1 Structure overview
The ISMS “Matrix” is implemented as a relational database
with menus, screen forms and printable reports in Microsoft Office Access 2000
Database format (*.mdb).database itself consists of two main tables, risk list
and common classifying elements lists (see appendix C). The tables are linked
on the scheme not by ID fields (as it is classically made in database
construction), but by the names of elements. This is arranged for better
flexibility in case of changes in data structures during the ISMS development
or customisation.first main table “Knowledge” (Тд_ЗНАНИЯ) contains the
information about the input normative documents and regulations. The second
main table “Tasks” (Ту_ЗАДАЧИ) contains the information about all the
dispatched tasks: current, planned and archived.assessment is performed by
forming asset-threat relations in the table “Risk list” (спис_риски). For quantitative estimations value
fields are provided in tables of assets (спис_активы) and threats (спис_угрозы). For
details see appendix C.
3.4.2 Classifying elements
The classification of sections from multiple documents as
well as the classification of tasks is implemented by the introduction of the
common classifying elements according to Domarev’s Matrix of system approach to
IS [2]. The classifying elements are listed below according to appendix C.
. Directions (напрямки);
. Objects (об’єкти);
. Group of bases (основи);
.1. Officials (співробітники);
.2. Documents (документи);
.3. Measures (заходи);
.4. Means (засоби);
. Stages (етапи);
. Group of stage contents (зміст етапів);
.1. Assets (активи);
.2. Threats (загрози);
.3. Requirements (вимоги);
.4. Solutions (вирішення);
.5. Implementations (впровадження);
.6. Control (контроль).detailed descriptions of each of the classifying elements are
presented further in this subsection.set of classifying elements contains
optional fields named “Level code 1” to “Level code 3” (Код рівня 1 - Код рівня 3). These fields are added for custom
sorting of the set in case there are many entries and they are needed to be
grouped. The filling of these fields is completely optional and does not affect
the performance of the ISMS.
. Directions (напрямки)element was initially intended to divide the IS by the types
of ISS operation. The division was made considering the specificity of IS
components and processes being protected. Presently, the best practice is to
match the IS directions with business directions, or business processes. For
example, if the bank provides card services, deposits and e-banking, it is recommended
to list these as “directions”.define directions it is needed to consider what
business directions does the target enterprise have and what major business
processes run at the target enterprise.set of directions depends completely on
the target enterprise or considered document. There are no standard directions,
so the user has to fill the list on his own. Nevertheless, it is recommended to
add “Whole enterprise” (Банк в цілому) or “All directions” (Всі напрямки) entries to the directions list. These entries might
be needed when there are enterprise-wide or even enterprise-independent
regulations.
. Objects (об’єкти)element
was not initially present in classic system approach to IS, but practical
implementation experience has shown the necessity of its introduction. The
objects are the major complex entities of the target organisation. The list of
these elements might include the core objects of the organisation’s business
processes.
To define the objects, it is needed to list the core elements of the
organisation’s business processes, not getting in detail.
The set of objects may include physical or information
systems, like “Computer network” (Комп’ютерна мережа), or “E-mail system” (Електронна пошта). It is also recommended
to add “Object-independent” (Окрема задача) entry
to the objects list. This entry might be needed when there are
object-independent or enterprise-wide regulations.
3. Group of bases (основи)group of classifying elements
corresponds to “Bases” group from classical system approach matrix (including
normative base, structure, measures and means). In classification of documents
and tasks within the ISMS, the table storing the list of structure officials (спис_сотр) is used twice: once to define the supervisor, and the
second time to select the responsible employee.
3.1. Officials (співробітники)element initially described the structure of organisation’s
officials and departments that were responsible for the provision of
information security. Presently, the list of officials contains all the
officers and departments involved in solution of the IS tasks, because it is
used to define both supervisors and the responsible. Practice shows that it is
frequent that non-security officials are drawn in the IS processes. For
example, according to the standard [3], the top management of the organisation
must perform several security tasks, among which are the roles distribution
among the employees and driving the importance of the IS management to
non-security divisions so that the productive cooperation between IS service
and other departments is ensured.is no criteria to define the officials that
will be involved in IS processes.fill the officials list, it is first needed to
list the IS department in person and in general. For the latter it is
recommended to use a record like “IS department” (Підрозділ інформ. безпеки). It is also recommended to add the
record for management in general like “Management” (Керівництво). Further, it will be needed to add
each employee or department that would be mentioned in the IS tasks or
documents. The cooperation with human resource department will be helpful to
have the list of employees and departments.
3.2. Documents (документи)this element represented the legislative,
normative-methodical and scientific base of documents that were involved in the
legislative aspects of information security. In the current ISMS implementation
this element defines the document, part of which is being stored in the
documentation module, or within the scope of which the task is
dispatched.compose the set of documents, it is needed to enter the names of all
the documents that regulate the information security at the target
organisation, plus the standards that are about to be implemented.short names
of the documents must be entered in the set. The names of the document groups
may optionally be added in case there are multi-document tasks or regulations,
for example “Regulations of the Cabinet of ministers” (Постанови Кабміну) or “International
documents” (Міжнародні
документи).
.3. Measures (заходи)in the classic system approach to IS, the set of measures is the set of
actions aimed at providing the information security at the target organisation.
These usually include measures executed at the creation of ISS, measures
executed in the process of exploitation of the ISS and the measures of general
profile.define the measures it is needed to check, what concrete processes and
procedures aimed at IS support occur in the target organisation.is no standard
set of measures, although the actions executed at organisations in order to
provide and support information security are similar. The set can be large,
including high- and low-level measures. One example of a high-level measure is
“Access control” (Контроль доступу) and of a low-level measure - “Connection time limit” (Обмеження часу підключення).
.4. Means (засоби)in the classic system
approach to IS, this set includes program-technical means and methods of IS.
They are the concrete tools used in IS or audit processes of the target
organisation or considered document.author considers it worth noting that the
set of means includes not only physical security items, but also the security
methods like “Testing methods” (Методи тестування). To determine the IS means of the target
organisation or considered document, it is needed to list all the concrete
tools and names of the methods that are used in IS processes.set of means
depends mostly on the target enterprise or considered document. Although there
is a great variety of standard IS means and methods, this set will be varying
largely depending on the size and business processes of the target
organisation. As for the documents, the high-level standards (including ISO27k
family, [3] and [4]) usually do not specify the concrete IS means. Common
practice for documents is general naming like “Cryptographic means” (Криптографічні засоби).
4. Stages (етапи)element is intended to divide the IS processes into major steps.
Initially, in the classic system approach to IS, the seven steps were formed
based on the methodologies of ISS creation existent at the time of the research
[2]. During the development of the ISMS “Matrix”, the need arose to adapt to
various standards. This pushed the author (and developer) to separate the seven
classical stages into a group of stage contents (зміст етапів) described below, and make the set
of stages variable.define the IS stages of the target organisation or the
considered document, it is needed to detect the major steps of ISS creation,
maintenance and development.ISMS users can employ the seven classical stages
(that coincide with the names of the elements listed below) or the stages
explicitly stated in the considered document. For example, the standard [3]
defines the model “Plan-Do-Check-Act” (Плануй-Виконуй-Перевіряй-Дій), so the stages set might consist of
four entries with optional sub-stages.
. Group of stage contents (зміст етапів)group of classifying elements
corresponds to “Stages” group from classical system approach matrix, including definition of assets to
be protected, definition of threats and information loss channels, risk
estimation, definition of requirements to the ISS, selection of IS means,
implementation of the selected means and methods of IS, control of the ISS
integrity and IS management.practical implementation experience has shown that each
stage of ISS creation and management has a broad varying set of sub-stages that
depends completely on the target organisation or considered document.
Nevertheless, risk assessment was separated into a distinct module, which does
not classify, but simply provide the approximate numerical estimations or
risks.
5.1. Assets (активи), in the classic system approach to IS, this element represented the
classified or sensitive information to be protected by an ISS. The information
is considered sensitive if its disclosure may cause damage to the vital
interests of the target organisation or to the personal safety of people. The
practical ISMS implementation experience has shown that it is needed to amend
the list of assets with everything that can be affected by IS threats. For
example, the Ukrainian branch standard [3] defines the assets as “everything
that has a value to the organisation”. This caused the appearance of such
entries as “Operating systems” (Операційні системи) or “Internetwork screen” (Міжмережевий екран).determine the list of
assets for the target enterprise or the considered document, it is needed to
name all the low-level entities, present in the target organisation or
mentioned in considered document, that may be affected by IS threats and thus
cause IS risks. It is worth noting that the set of assets differs from the set
of objects described above in the sense that objects are complex entities of
the business processes, and the assets are more concrete and low-level entities
that are affected by IS threats. For example, when “Computer network” (Комп'ютерна мережа) is an object with
possibility to become an asset, “Cryptographic keys” (Криптографічні ключі) can only be an
asset.list of assets depends completely on the structure and peculiarities of
the target enterprise or the considered document, so there is no standard set
of assets. The user has to fill it on his own. Some examples of the assets are
“System files” (Системні
файли),
“Control logs” (Журнали
контролю) and
“Personal data” (Персональні
дані). It is
recommended to add “All assets” (Всі активи) entry for the case of enterprise-wide tasks or regulations.
The entries in the set of assets contain the numerical field damage (збиток). Upon the entry of an asset, a
value of damage in case of asset collapse has to be defined in order to get the
numerical risk estimations later. It is proposed to scale the damage values
from “high” to “low” with corresponding conventional marks 5 to 1 respectively.
Nevertheless, the user may estimate the damage in case of asset collapse by
concrete monetary amounts of loss.
5.2. Threats (загрози), in the classic system approach to IS, this element represented the
process of detection of threats and sensitive information loss channels.
However at practical implementation of the ISMS “Matrix”, it was decided to
move the threat detection process itself to the set of stages (етапи), and let the element “threats” (загрози) contain the list of
threats detected at the target organisation or mentioned in the considered
document.detect the IS threats of the target organisation, any method is
applicable, from theoretical estimation to professional penetration test or
expert commission. Such detection process can be performed either at the stage
of information system planning, or at the stage of its functioning.exist some
lists of threats issued by information security companies, but they include
universal sets of threats, most of which is impossible or unimportant to the
target organisation, or not mentioned in considered document. It is recommended
to fill the set of threats gradually, adding entries at first mentioning of a
concrete threat.entries in the set of threats contain the numerical field
frequency (частота). Upon the entry of a threat, a value of its appearance frequency has to be
defined in order to get the numerical risk estimations later. It is proposed to
scale the frequency values from “frequent” to “very rare” with corresponding
conventional marks 5 to 1 respectively. Nevertheless, the user may estimate the
frequency of threat appearance in by concrete probability value, which is usually inaccurate and hard
to determine due to peculiarities of concrete organisation and its business
processes.
5.3. Requirements (вимоги)in the classic system approach to IS, this element represents the set of
requirements to the information security system. These requirements may refer
to the scope of certain ISS functions, levels of certain characteristics. In
the proposed ISMS implementation, the set of requirements contains the titles
or types of the regulations that define the requirements to the ISS in
question.define the requirements to the ISS of the target organisation without
assistance, it is needed to decide which security measures are planned to be
used, what is the cost of the available hardware and software security means,
how effective are the available security measures and means, how vulnerable are
the ISS subsystems, is there a possibility to carry out a risk analysis. In
case of implementing a certain standard using ISMS “Matrix”, the requirements
can be taken directly from the considered document.set of requirements can be
taken from the considered document, because they are usually explicitly stated
there. The documents can be the technical tasks for the ISS creation, target organisation’s
security policy or a standard. For example the Ukrainian branch standard [3] is
itself the set of demands to an ISMS. In such case the entries of the set of
requirements will be the titles of corresponding document sections.
5.4. Solutions (вирішення)element initially represented the process of selection of the
means and methods that will provide the achievement of the compliance with the
set requirements. In the proposed ISMS implementation, the set of solutions
represents the complex means and methods of information security (usually,
mature commercial products) used to achieve the compliance with the
requirements described above.define the set of solutions, firstly it is needed
to decide what means and methods should be used to attain the established
requirements in the target organisation or the considered document. Secondly,
it is needed to explore the IS solutions market and find those that provide the
most of demanded functions or best comply with the set requirements.exist a
very large number of IS solutions. Each target organisation should select the
solutions according to its needs, implementation potential and budget. The IS
standards usually do not specify the concrete solutions in order to give some
freedom (and thus ease) in implementation. It is the best practice if the set
of solutions (вирішення) contains concrete names
of the IS products used at the target enterprise, but general names like
“Application of controls” (Застосування контролів) or “Access limitation” (Обмеження доступу) are also available.
5.5. Implementations (впровадження)element initially designated the
actions taken in order to implement the selected IS solutions (that in turn
satisfy the set requirements). The implementation may occur at different IS
levels (administrative, organisational, technical) and at all stages (design,
construction, testing or upgrade of an ISS).define the set of implementation
entries, it is needed to decide what methods and organisational arrangements
will be used to implement the selected IS solutions at the target
organisation.set of implementations depends on the structure and other
peculiarities of the target organisation and its personnel in particular. It is
recommended to state the decree and control of the target organisation’s management
concerning the IS implementation, because practical implementation experience
shows that personnel’s unwillingness is one of the strongest obstructive
factors on the way to establishment of the corporate information security. It
is recommended to list the general names of the implementation procedures, like
“Personnel training” (Навчання персоналу) or “Equipment tuning” (Налаштування обладнання).
.6. Control (контроль)
As in the classic system approach to information security,
this element represents the processes of the ISS integrity control and IS
management. These processes encompass a wide scope of functions ranging from
strictly-technical, like “Control of copying” (Контроль копіювання) to high-level
managerial, like “Control of IS responsibilities” (Контроль відповідальностей за ІБ). The Ukrainian branch
standard [4] defines controls as “means of risk management that include
policy, procedures, directives, practice or organisational structures, which
can have administrative, technical, managerial or legal character”. But in the
proposed ISMS implementation control has the broader aspect, aimed not at risk
management, but at the maintenance of IS and implementation of certain
regulations. Thus risk control becomes a part of more complex IS mechanism.
To define the set of control it is necessary to compose the
list of procedures that ensure the integrity of the target organisation’s ISS,
or check and manage the implementation of the considered document.security
standards like [4] sometimes list the control entries explicitly, but the users
can also fill the control set by all management and testing IS processes that
take place at the target organisation. The list may include names of control
groups with sub-controls, like “Control of personnel” (Контроль персоналу) and “Control of
employment” (Контроль
прийому на роботу) respectively.the sets of values in each of the classifying elements are
formed by the end users for the target organisation or the considered document,
so the obtained system complies both with the system approach to IS and the
business processes of the target organisation, having the structure matching
the system approach and the filling matching the target organisation and
considered documents.the example if the end users have all the sets filled with
minimal necessary amounts of items, i.e. that each task or document record can
be classified at least in general. In this case the system will have the
following elements of the system approach to IS:
1. Bases, consisting of the documents, employees, measures
and means that exist in the target organisation;
2. Directions, corresponding to target organisation’s
major business processes;
. Seven classical stages of the system approach to IS
that have their results listed (for example, the asset definition as the first
stage results in the list of assets);
. The custom list of stages that represents the
target organisation’s IS process.
3.4.3 Main data storages
The main storages of the database in ISMS “Matrix” are the
tables “Tasks” (Ту_ЗАДАЧИ) and “Knowledge” (Тд_ЗНАНИЯ).table “Tasks” (Ту_ЗАДАЧИ) contains two sets of
fields: the group of classifying fields and the ones that constitute the
operational task itself. The classifying fields group places each task in the
systematised framework of the system approach to IS. The fields that constitute
the task are listed below:
1. “Date set” (Коли поставлена) - the date of task setting;
2. “Execution term” (Строк виконання) - the final date of the
task execution;
. “Status” (Статус) - the general state of the task (current, urgent,
cancelled, archived, etc.);
. Date “Updated” (Оновлена) - the date of the last changes made
to the task;
. “Task description” (Опис задачі) - the list of necessary actions;
. “Executors” (Виконавці) - regular and involved executors of the task and
their contact information (if more than one employee is involved in execution);
. “State” (Стан) - the degree of execution of the task and the list of
performed actions and involved measures;
. “Problems” (Проблеми) - questions and obstacles appeared during the execution of
the task;
. “Remarks” (Зауваження) - short remarks of the supervisor or management;
. “Supplementary” (Додатково) - hyperlink to supplementary
information;
. “Man-hours” (Люд-год) - number of man-hours given to execute the task.
The second main data storage in the database structure of the
ISMS “Matrix” is the table “Knowledge” (Тд_ЗНАНИЯ). Its strings are intended to
store the sections of documents that can be referred entirely to a certain
place of the system approach to IS, i.e. have assigned one of each classifying
elements. In case when the document is small and has a narrow coverage (like a
decree or a standard order), it can be stored in one record of the table
entirely. The table “Knowledge” (Тд_ЗНАНИЯ) contains two sets of fields: the
group of classifying fields and the ones that constitute the document section
itself. The classifying fields group places each document section in the
systematised framework of the system approach to IS. The fields constituting
the document section are listed below:
1. Shortly (Коротко) - the short heading of the document section;
2. Completely (Повно) - the full heading of the document section;
. Description (Опис) - description of the document section, including annotation
or notes concerning the section content;
. Contents (Зміст) - the full content of the document section. The field can
contain only a small note if the link to the document file is used (see next
item);
. Reference (Посилання) - hyperlink to supplementary information or the file with the
document itself (in this case the document content can be updated independently
of the ISMS).
3.4.4 Program modules
The implementation of the ISMS “Matrix” required the
development of program modules in Microsoft Visual Basic for Applications
language (MS VBA). Such modules were used for forms and reports. One module was
independent and contained the shared custom functions. This module is presented
in appendix E as an example.
3.5 Interfaces of the ISMS
.5.1 Main menu
The interaction of the end users with the ISMS “Matrix”
starts from the main menu (see fig. 3.1), which is automatically opened at the
start-up. The following functions are accessible from the main menu.
1. Management - operational tasks (Керування - оперативні задачі) - open the form
“Detailed tasks information” (Детальна інформація щодо задач) to enter or edit the operational
tasks;
2. Knowledge - documents (Знання - документи) - open the form
“Knowledge - documents input” (Знання - Введення документів) to enter or edit the documents or
their sections;
 . 3.1. The main menu of the ISMS
“Matrix”
. 3.1. The main menu of the ISMS
“Matrix”
3. Risks estimation (Оцінка ризиків) - open the pivot table with the
same name that presents the risks considered at the target enterprise;
4. Statistics of tasks and knowledge (Статистика задач та знань) - open the form
“Statistics” (Статистика) to call pivot tables on
various aspects of operational tasks and knowledge;
. Conditions of records selection for reports or
filters (Умови
відбору записів для звітів/фільтрів) - open the form “Selection conditions” (Умови відбору) to select the filtering
criteria used in input forms, compiled documents and task reports;
. Formation of documents or reports (Формування документів /
звітів) -
open the form with the same name to produce the reports on operational tasks or
compile the documents by various selections;
. Edit the elements lists (Редагувати списки елементів) - open the form
“Elements lists” (Списки елементів) to add or edit the
entries of the classifying elements and statuses of the operational tasks;
. Exit (Вихід) - close the ISMS.detailed description of the listed functions
is presented below.
3.5.2 Form “Detailed tasks information”
The form “Detailed tasks information” (Детальна інформація щодо задач) is opened from the main
menu of the ISMS “Matrix”. The fig. 3.2 presents the overview of the form. The
fields on the form are arranged into two groups - the ones that constitute the
operational task itself on the left hand side and the group of classifying
fields on the right hand side.
 . 3.2. The form “Detailed tasks
information” of the ISMS “Matrix”
. 3.2. The form “Detailed tasks
information” of the ISMS “Matrix”
field “Task code” (Код задачі) contains the task ID and is assigned automatically.
The task ID may be used for fast task search, because the pivot tables on the
tasks state the task IDs.date field “Set” (Коли поставлена) contains the date of task setting and is assigned
automatically on task record creation. Nevertheless, the users can change the
date in case the task was set earlier than entered into the ISMS.date field
“Execution term” (Строк виконання) contains
the final
date of the task execution. By this field the expiration of the task is
detected. If the task is unlimited in time, the field may be left blank.
The numeric field “Man-hours” (Людино-годин) contains the estimated number of man-hours given to execute the task.
The date field “Information updated” (Інформація оновлена) contains the date of the last changes made to
the task. The field is updated automatically upon any changes made to the
record, but it can be also modified by the users.text field “Executors,
contacts” (Виконавці,
контакти) contains the names of the regular
and involved executors of the task and their contact information, if more than
one employee is involved in the execution of the task.combo list field “Status”
(Статус) classifies the general state of the task
(current, urgent, cancelled, archived, etc.). The field values can be added and
edited using the form “Elements lists”, opened from the main menu of the
ISMS.hyperlink field “Supplementary” (Додатково) contains the hyperlink to supplementary information on the task. The hyperlink is
edited using the “Hyperlink” section of the field’s context menu.
The text field “Task description and measures” (Опис задачі та заходи) contains the list of actions, necessary to
accomplish. If the task is aimed at compliance with a certain document, the
field can duplicate the title of the corresponding document or its relevant
section.text field “Directives and execution state” (Настанови та стан виконання) describes the degree of execution of the task,
the list of performed actions and involved measures. It is recommended to append
the short notes during the task execution, starting each note with the
appending date. The field may also contain the detailed instructions concerning
the task execution.text field “Problems” (Проблеми) lists the questions and obstacles
appeared during the execution of the task that should be addressed to the
supervisor of the task or higher managers by the special report.text field
“Remarks” (Зауваження) contains the short remarks of the
supervisor or management concerning the solution of the appeared problems. This
field can also be used by management of the task the supervisor to express the
commentaries of high importance.is a group of three optional fields named
“Levels” (Рівні), situated in the top
central part of the form. These fields are added for custom sorting of the task
records within objects in case there are many entries and they are needed to be
grouped.print buttons “and are situated above the group of classifying fields
on the right hand side of the form. The button “Print current task” (Друк поточної задачі) prints the task record
that is currently displayed in the form. The button “Print task template” (Друк шаблона задачі) prints the template of
an operational task record for handwritten filling (this is intended to be used
if managers do not have direct access to the ISMS interfaces).classifying
fields’ meanings and descriptions are presented above in the subsection 3.4.2
“Classifying elements”.form contains a record filter which is opened by a
button “Conditions of records selection” (Умови відбору записів) on the right side of the
form. The operation of the filter is described in the subsection 3.5.4 “Input
forms filter”.
3.5.3 Form “Knowledge - documents input”
The form “Knowledge - documents input” (Знання - Введення документів) is opened from the main
menu of the ISMS “Matrix”. The fig. 3.3 presents the overview of the form. The
fields on the form are arranged into two groups - the ones that constitute the
document section itself on the left side and the group of classifying fields on
the right side.text field “Short heading” (Короткий заголовок) contains the short
heading of the document section or knowledge element. It may be descriptive or
contain the common name of the document.text field “Full heading” (Повний заголовок) contains the full
official heading of the document section or knowledge element. For example, for
the standard [3] the full heading is “Інформаційні технології. Методи захисту. Система
управління інформаційною безпекою. Вимоги (ISO/IEC 27001:2005, MOD)”, and the short heading is “ГСТУ СУІБ 1.0/ISO/IEC 27001:2010”. The field is also used for
grouping the document sections or knowledge elements in the document
compilations.
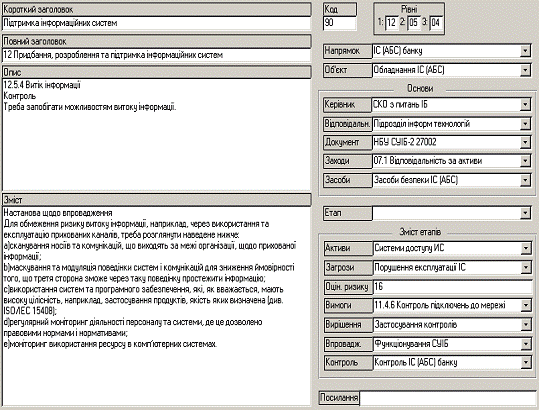 . 3.3. The form “Knowledge -
documents input” of the ISMS “Matrix”
. 3.3. The form “Knowledge -
documents input” of the ISMS “Matrix”
text field “Description” (Опис) contains the description of the
document section or knowledge element, including annotation or notes concerning
the content. It is important to fill this field because the higher level IS
policy formed by the ISMS is compiled of descriptions of the document sections
and knowledge elements.text field “Contents” (Зміст) contains the full content of the
document section or knowledge element. The field can contain only a small note
if the link to the document file is used in the field “Reference (Посилання)”. Please refer to the
next paragraph for details.hyperlink field “Reference” (Посилання) contains the hyperlink to supplementary
information source or the file with the document or knowledge element itself. The field is
situated under the group of the classifying element fields at the bottom-right
side of the form. It is possible to link the knowledge database record to an
external document file. In this case the content of the document can be altered
independently of the ISMS.
The field “Code” (Код) contains the ID of the document section or knowledge
element and is assigned automatically. The ID field may be used for fast
knowledge search, because the pivot tables on knowledge state the IDs.is a
group of three optional fields named “Levels” (Рівні), situated in the top-right part of
the form. These fields are added for custom sorting of the task records within
a document in case there are many entries and they are needed to be grouped. If
the document subsections have numeration, it is recommended to duplicate the
numeration in the field group “Levels”.classifying fields’ meanings and
descriptions are presented above in the subsection 3.4.2 “Classifying
elements”.form contains a record filter which is opened by a button “Conditions
of records selection” (Умови відбору записів) on the right side of the form. The operation of the filter
is described in the subsection 3.5.4 “Input forms filter”.
3.5.4 Input forms filter
The two input forms of the ISMS “Matrix”, “Detailed tasks
information” (Детальна
інформація щодо задач) and “Knowledge - documents input” (Знання - Введення документів) contain a record filter
which is opened by a button “Conditions of records selection” (Умови відбору записів) on the upper-right side
of each form. The fig. 3.4 presents the overview of the filter.the press of a
button “Conditions of records selection”, the filter switch appears on the
input form, and the form “Selection conditions” (Умови відбору) is opened automatically to select
the filtering criteria. After the selection conditions are set in the
corresponding fields, it is possible to switch back to the initial input form
by pressing one of the buttons in the upper-right side of the “Selection
conditions” form. It is possible to return to the “Selection conditions” form
to change the filtering criteria by pressing the button “Conditions of records
selection” on the input form.
 . 3.4. The input forms filter of the
ISMS “Matrix”
. 3.4. The input forms filter of the
ISMS “Matrix”
filter is capable to select the records by only one criterion
at a time, which is selected by a radio buttons group named “Mode” (Режим). The following filtering modes are
present, each selecting the records where the value in the corresponding field
matches the one specified on the form “Selection conditions”.
. “Show all” (Показати всі) - lists all records without disabling the filter;
. “Responsible” (Відповідальний);
. “Document” (Документ);
. “Measures” (Заходи);
. “Means” (Засоби);
. “Assets” (Активи);
. “Threats” (Загрози);
. “Requirements” (Вимоги);
. “Solutions” (Вирішення).button “Refresh selection” (Оновити вибірку) is used to re-filter in
the selected mode. This action is usually needed in the two following
situations. First, when some of the filtered records have been changed and do
not fit the selection criterion anymore. Second, when the selection criterion
has been changed and it is needed to filter the records in the same mode
again.button “Conditions of records selection” (Умови відбору записів) is used to enable the
filter and to switch to “Selection conditions” form. It is also possible to
switch to the form and back by the standard means of MS Access.button “Disable
filter” (Вимкнути
фільтр)
cancels the filtering selection, hides the filter controls and closes the form
“Selection conditions”, unless that form is used by another filter or report
formation.
3.5.5 Pivot table “Risks estimation”
The form “Risks estimation” (Оцінка ризиків) is opened from the main
menu of the ISMS “Matrix”. The fig. 3.5 presents the overview of the pivot
table. The form visualises the distribution of risks among the assets of the
target organisation.
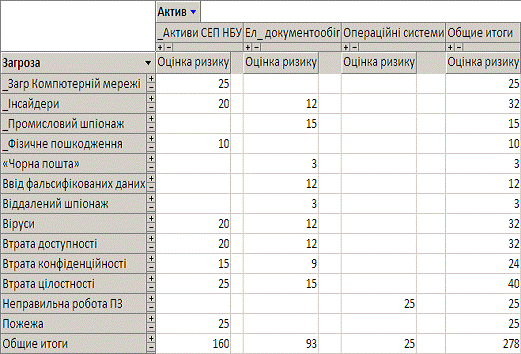 . 3.5. The pivot table “Risks
estimation” of the ISMS “Matrix”
. 3.5. The pivot table “Risks
estimation” of the ISMS “Matrix”
pivot table presents the distribution of risks as the
correlation between threats and assets of the target organisation. The total
risk estimations are provided for each threat, each asset and the whole
organisation.values of the risk estimations can be conventional or be measured
in terms of financial losses. The detailed description of the risk estimation
mechanism is presented below in subsection 3.6.3 “Risk assessment”.can be applied
to the pivot chart by assets and threats. The display of certain elements of
assets or threats is controlled by the standard means of MS Access for pivot
charts. To enter the list of displayed elements, it is necessary to click the
triangle next to the name of the element header. On the fig. 3.5 such
filter-enabling triangles can be seen near the row heading “Asset” (Актив) and the column heading “Threat” (Загроза). The filters of the
pivot table can be applied simultaneously.
3.5.6 Form “Statistics of tasks and knowledge”
The form “Statistics of tasks and knowledge” (Статистика задач та знань) is opened from the main
menu of the ISMS “Matrix”. The fig. 3.6 presents the overview of the form. The
form calls the pivot charts that display the general overviews of the IS state
at the target enterprise from the different perspectives.
 . 3.6. The form “Statistics of tasks
and knowledge” of the ISMS “Matrix”
. 3.6. The form “Statistics of tasks
and knowledge” of the ISMS “Matrix”
information from the pivot tables can be used to facilitate
the ISS audit process. The statistics are provided for both tasks and documents
sections of the ISMS.list of pivot tables opened from the form is the
following.
1. Group “Statistics of tasks” (Статистика задач):
.1. Tasks by the Matrix (Задачі по Матриці);
1.2. Tasks by employees (statuses) (Задачі по співробітникам (статусам));
1.3. Tasks by objects (Задачі по об'єктам);
1.4. Tasks by supervisors (Задачі по керівникам);
1.5. Expired tasks (Прострочені задачі);
2. Group “Statistics of knowledge” (Статистика знань):
2.1. Assets by responsible (Активи за відповідальними);
2.2. Assets by documents and responsible (Активи за документами та
відповідальними);
2.3. Distribution of requirements by responsible (Розподіл вимог за
відповідальними).detailed
descriptions of the listed pivot tables are presented below in the subsection 3.5.10 “Pivot tables of
statistics”.
3.5.7 Form “Selection conditions”
The form “Selection conditions” (Умови відбору) can be opened either from the main
menu of the ISMS “Matrix”, tasks and knowledge input forms, or “Formation of
documents or reports” (Формування документів / звітів) form. The fig. 3.7 presents the overview of the
form. The fields on the form duplicate the group of the classifying fields in
the input forms.combo list boxes of the classifying elements are intended to
store the selection conditions for the tasks and knowledge input forms or
formation of documents and reports. For example, if the field “Document” (Документ) is set to “НБУ СУІБ-1
27001” (the short name of [3]), then when the input form filters will be
switched into the “Document” mode, all the records having “НБУ СУІБ-1 27001” in
the “Document” field will be selected. This also applies to reports involving
selection by document.
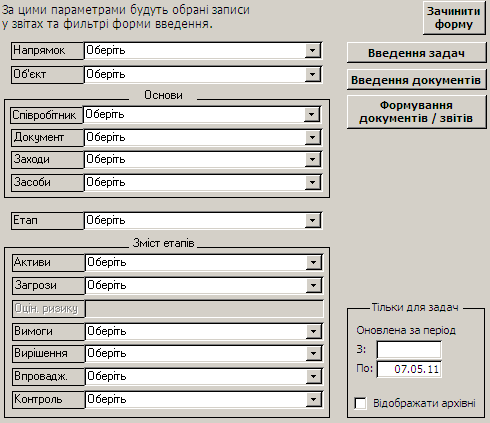 . 3.7. The form “Selection
conditions” of the ISMS “Matrix”
. 3.7. The form “Selection
conditions” of the ISMS “Matrix”
form contains the group of fields “For tasks only” (Тільки для задач), including updating
range limiters and “Show archived” (Відображати архівні) checkbox. The group is situated in the lower-right
part of the form.date fields “From” (З) and
“Till” (По) specify the range of
task updating date. Both fields must be specified to use the task reports
involving a time period. If the starting range is unknown, the users can enter
any early date (like 01.01.1900).button “Close the form” (Зачинити форму) closes the form in no
forms depend on it. For example, if a filter is on in the tasks input form, the
“Selection conditions” form would not close upon the button press.button “Tasks
input” (Введення
задач) opens
the form “Detailed tasks information” (Детальна інформація щодо задач) and enables its filter
automatically.button “Documents input” (Введення документів) opens the form “Knowledge -
documents input” (Знання - Введення документів) and enables its filter automatically.button
“Formation of documents or reports” (Формування документів / звітів) opens the form with the same name
to select a report or document compilation based on selected criteria.
3.5.8 Form “Formation of documents or reports”
The form “Formation of documents or reports” (Формування документів /
звітів) is
opened either from the main menu of the ISMS “Matrix” or from the form
“Selection conditions” (Умови відбору). The fig. 3.8 presents the overview of the form. There are
three groups of elements on the form situated vertically. The topmost group has
the elements serving for common purposes. The next group forms the task
reports. The group at the lower side of the form sets the document
compilations.
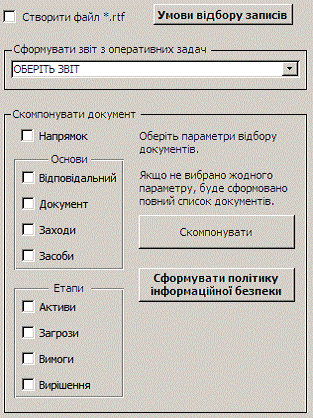 . 3.8. The form “Formation of
documents or reports” of the ISMS “Matrix”
. 3.8. The form “Formation of
documents or reports” of the ISMS “Matrix”
The button “Conditions of records selection” (Умови відбору записів) opens the corresponding
form.checkbox “Create *.rtf file” (“Створити файл *.rtf”) triggers the export of selected report to an
external file.list “Form the report on operational tasks” (Сформувати звіт з оперативних
задач) is
intended to select the report to be produced. The report is made immediately
after the selection of the corresponding item in the list. The following
reports are available for the operational tasks section of the ISMS “Matrix”.
1. All tasks (Всі задачі);
2. Archived tasks over a period (Архівні задачі за період);
3. Expired tasks for today (Прострочені задачі на сьогодні);
4. Tasks by direction (Задачі по напрямку);
5. Tasks by direction and responsible (Задачі по напрямку та
відповідальному);
6. Tasks by direction and object (Задачі по напрямку та об'єкту);
7. Tasks by direction over a period (Задачі по напрямку за період);
8. Tasks over a period by responsible (Задачі за період по
відповідальному);
9. Tasks over a period by supervisor (Задачі за період по
керівнику);
10. Tasks over a period by object (Задачі за період по об'єкту);
11. Tasks over a period by object and responsible (Задачі за період по об'єкту
та відповідальному);
12. All problems (Всі проблеми);
13. Problems by responsible (Проблеми по відповідальному);
14. Problems by object (Проблеми по об'єкту);
15. Problems over a period (Проблеми, що виникли за період);
16. Tasks by stage (Задачі по етапу);
17. Tasks by stage and direction (Задачі по етапу та напрямку).
The reports involving selection for the time period assume
the range of updating dates and do not take into account the records with empty
“Updated” fields.group “Compile the document” (Скомпонувати документ) contains the set of
knowledge selection criteria checkboxes and two document compilation buttons.
The knowledge can be selected from the database by any combination of the
criteria. If none of the criteria is selected, the full list of documents and
knowledge will be compiled.button “Compile” (Скомпонувати) launches the compilation of the
document according to the ticked checkboxes of selection criteria. If none of the
criteria are selected, the full list of documents and knowledge will be
compiled.
The button “Form the information security policy” (Сформувати політику інформаційної
безпеки)
launches the formation of the high-level IS policy based on all the stored knowledge. The description
of the formed policy is presented in the subsection 3.6.4 “Information security
policy formation” below. The sample page of the formed IS policy is presented
in appendix D.
3.5.9 Form “Elements lists”
The form “Elements lists” (Списки елементів) is opened from the main menu of the ISMS “Matrix”. The fig.
3.9 presents the overview of the form. The form is intended to edit the entries
of classifying elements and statuses of operational tasks.
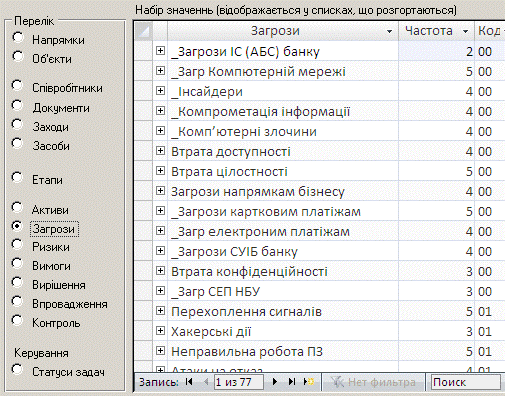 . 3.9. The form “Elements lists” of
the ISMS “Matrix”
. 3.9. The form “Elements lists” of
the ISMS “Matrix”
left side of the form is the group of radio buttons that
select the list to edit. The selectors are grouped in the same way as are the
classifying fields in the input forms. To the right side of the form the table
of the selected list is loaded. The following list selectors are present on the
form:
. Directions (Напрямки);
. Objects (Об’єкти);
. Officials (Співробітники);
. Documents (Документи);
. Measures (Заходи);
. Means (Засоби);
. Stages (Етапи);
. Assets (Активи);
. Threats (Загрози);
10. Risks (Ризики);
11. Requirements (Вимоги);
. Solutions (Вирішення);
. Implementations (Впровадження);
. Control (Контроль);
. Task statuses (Статуси задач).descriptions of the classifying
elements are presented in the subsection 3.4.2 “Classifying elements”. The
description of risk list is presented in the subsection 3.6.3 “Risk assessment”.
3.5.10 Pivot tables of statistics
.5.10.1 Pivot table “Statistics of tasks by the
Matrix”
The pivot table “Statistics of tasks by the Matrix” (Статистика задач по Матриці) is opened from the form
“Statistics of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”. The fig. 3.10
presents the overview of the pivot table. The table displays the distribution
of operational tasks by the Matrix of the system approach to IS. The two
differences between this presentation and the classic Matrix are the absence of
“Bases” group (because the bases are represented by several database fields)
and the use of custom names for the directions and stages.
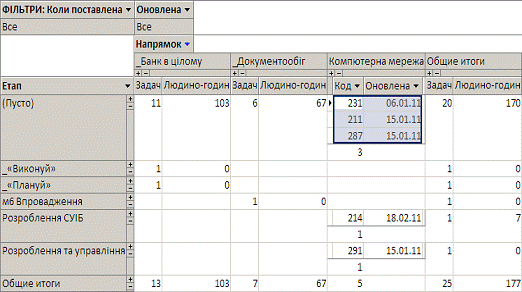 . 3.10. The pivot table “Statistics
of tasks by the Matrix” of the ISMS “Matrix”
. 3.10. The pivot table “Statistics
of tasks by the Matrix” of the ISMS “Matrix”
pivot table presents the total quantities of tasks and
approximate amount of man-hours needed for their completion. The details are
task IDs and their updating dates. To open the details for a certain direction
or stage, it is needed to press the “plus” sign near the name of corresponding
row or column. On the fig 3.10 the details are opened for the direction
“Computer network” (Комп’ютерна мережа).the filters by the names of directions and stages (opened by pressing triangle
near the element’s mane), the pivot table can also be filtered by the date of
task setting and the date of updating. All the filters can be applied
simultaneously.
.5.10.2 Pivot table “Task statuses over a period”
The pivot table “Task statuses over a period” (Статуси задач за період) is opened from the form
“Statistics of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”. The table is
intended to present the distribution of tasks by the responsible
employees.pivot table presents the total quantities of tasks and approximate
amount of man-hours needed for their completion. The details are the objects
referred by the tasks and the task IDs. To open the details for a certain row
or column, it is needed to press the “plus” sign near its name.
Except the filters by the names of statuses and responsible (opened by
pressing triangle near the element’s mane), the pivot table can also be
filtered by the date of task updating. All the filters can be applied
simultaneously.
3.5.10.3 Pivot table “Tasks by
objects”
The pivot table “Tasks by objects” (Задачі по об'єктам) is opened from the form “Statistics
of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”. The table
presents the complex distribution of tasks given to different employees by
objects. The objects are grouped by the directions. To view the total results
for a certain direction, it is needed to press the “plus” sign to the left of
its name.pivot table presents the total quantities of tasks and approximate
amount of man-hours needed for their completion. The details are the task
statuses and the task IDs. To open the details for a certain row or column, it
is needed to press the “plus” sign near its name.
Except the filters by the names of responsible, directions and objects
(opened by pressing triangle near the element’s mane), the pivot table can also
be filtered by the date of task updating and task status. All the filters can
be applied simultaneously.
3.5.10.4 Pivot table “Tasks by supervisors”
The pivot table “Tasks by supervisors” (Задачі по керівникам) is opened from the form
“Statistics of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”. The table
presents the complex distribution of tasks given by the different supervisors. The tasks
are grouped by objects, which in turn are grouped by responsible officials. To view the total results
for a certain responsible, it is needed to press
the “plus” sign to the left of the corresponding name.pivot table presents the
total quantities of tasks and number of expired tasks. The details are the task
IDs, “Expired” labels, dates of the task setting and execution terms. To open
the details for a certain row or column, it is needed to press the “plus” sign
near its name.
Except the filters by the names of supervisors, responsible and
directions (opened by pressing triangle near the element’s mane), the pivot
table can also be filtered by the date of task setting and task status. All the
filters can be applied simultaneously.
3.5.10.5 Pivot table “Expired tasks”
The pivot table “Expired tasks” (Прострочені задачі) is opened from the form “Statistics of tasks and
knowledge” (Статистика
задач та знань)
of the ISMS “Matrix”. The table presents the number of expired tasks on the
objects which in turn are grouped by the responsible officials.details of the
pivot table are task IDs, dates of the task setting and execution terms. To
open the details for a certain row or column, it is needed to press the “plus”
sign near its name. To view the total results for a certain responsible, it is needed to press
the “plus” sign to the left of the corresponding name.
Except the filters by the names of responsible and objects (opened by
pressing triangle near the element’s mane), the pivot table can also be
filtered by the date of task setting and task status. All the filters can be
applied simultaneously.
3.5.10.6 Pivot table “Assets by
responsible”
The pivot table “Assets by responsible” (Активи за відповідальними) is opened from the form
“Statistics of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”. The fig. 3.11
presents the overview of the pivot table. The table presents the distribution
of IS measures by directions, then objects, then assets.
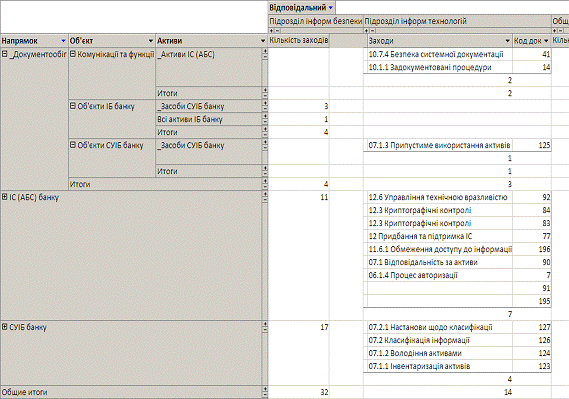 . 3.11. The pivot table “Statistics
of tasks by the Matrix” of the ISMS “Matrix”
. 3.11. The pivot table “Statistics
of tasks by the Matrix” of the ISMS “Matrix”
pivot table presents the total quantities of IS measures. The
details are the names of the measures and the corresponding knowledge IDs. To
open the details for a certain row or column, it is needed to press the “plus”
sign near its name. To view the total results for a certain object or direction, it is needed to press
the “plus” sign to the left of the corresponding name.pivot table can be
filtered by the names of the responsible, assets, objects and directions
(opened by pressing triangle near the element’s mane). All the filters can be
applied simultaneously.
3.5.10.7 Pivot table “Assets by
documents and responsible”
The pivot table “Assets by documents and responsible” (Активи за документами та
відповідальними) is opened from the form “Statistics of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”.
The table represents the distribution of assets mentioned in all the documents
of the knowledge base between the responsible officials grouped by the
directions.pivot table presents the total quantities of assets. The details are
the names of the assets and the corresponding knowledge IDs. To open the
details for a certain row or column, it is needed to press the “plus” sign near
its name. To view the total results for a certain direction, it is needed to press the “plus”
sign to the left of its name.pivot table can be filtered by the documents,
responsible officials and directions (opened by pressing triangle near the
element’s mane). All the filters can be applied simultaneously.
3.5.10.8 Pivot table “Requirements
by responsible”
The pivot table “Requirements by responsible” (Вимоги за відповідальними) is opened from the form
“Statistics of tasks and knowledge” (Статистика задач та знань) of the ISMS “Matrix”. The table
presents the distribution of the requirements of the implemented documents or
knowledge elements by responsible officials.pivot table presents the total
quantities of requirements. The details are the names of the requirements and
the corresponding knowledge IDs. To open the details for a certain row or
column, it is needed to press the “plus” sign near its name.pivot table can be
filtered by the documents and responsible officials (opened by pressing
triangle near the element’s mane). All the filters can be applied
simultaneously.
3.6 Operation of the ISMS
.6.1 Filling recommendations
To ensure the most effective operation of the ISMS “Matrix”
in partial uncertainty, the author recommends starting the exploitation of the
system by filling the lists of classifying elements with all known items
independently of tasks or documents, i.e. enter the initially known description
of the target organisation.lists of classifying elements can be edited in
“Elements lists” (Списки елементів) form called form the main menu of the ISMS by the item
“Edit the elements lists” (Редагувати списки елементів). It is possible to start with any
classifying element except “Risks” (Ризики), because
that list is built of elements from “Assets” (Активи) and “Threats” (Загрози). The logic of this dependence is
described below in the subsection 3.6.3 “Risk assessment”.recommendations
concerning definition of entries and presence of recommended values for each of
the classifying elements are presented above in the subsection 3.4.2
“Classifying elements”.
In the process of further exploitation the lists of
classifying elements are subject to changes, which is a normal part of the ISMS
integration process. The mentioned changes may be caused primarily by the
extension of knowledge about the target organisation, or by the changes in
business processes or in the structure of the target organisation.task statuses
list has to be filled just before the beginning of the tasks input. The list
initially has some values that are system-critical, but the practical
implementation experience suggests that it will be needed to add statuses for
current, important and planned tasks.the lists of elements are ready, it is
possible to start the input of tasks and knowledge. These two main branches can
usually be filled independently and in parallel, but when the ISMS is used to
implement a certain standard, it is better to start with filling the “Knowledge
- documents” (Знання
- документи) section.entering the
documents with the “Knowledge - documents input” (Знання - Введення документів) form it is better to
split the big document into small sections, which can be entirely classified by
a certain item in each classifying element. If the document is initially
divided into sections and subsections, it is recommended to enter each smallest
subsection as a separate knowledge record. This will increase the efficiency of
formation of security policy, post instructions or other documents. The section
“Knowledge - documents” is also intended to store any kind of reference
information on information security (classified as “knowledge”).operational tasks
are entered and edited through the form “Detailed tasks information” (Детальна інформація щодо
задач). It is
a usual case, when third party is involved in the operational task execution
process, or when there are more than one executor. For such case, the involved
officials can be listed in “Executors, contacts” (Виконавці, контакти) field. If the task is
aimed at compliance with a certain document, the field “Task description and
measures” (Опис
задачі та заходи) can duplicate the title of the corresponding document or its relevant
section. The short reports on the task execution progress should be appended in
the field “Directives and execution state” (Настанови та стан виконання). The problems that have
to be addressed to the management should be listed in the field “Problems” (Проблеми).it is hard to classify
the knowledge or task record with present classifying elements, it is possible
to add new values to the lists. Nevertheless, it is wise to analyse the
absolute necessity of such addition and forecast whether the new value of a
classifying element can be used by other records. Flooding the classifying
elements lists will strongly decrease the system approach classification
efficiency and may cause incomplete selections.
3.6.2 Reporting
The “Matrix” can produce analytical reports as documents
(both for printing and export to MS Word). The report formation is performed
the following way:
1. The selection parameters are chosen on the form
“Selection criteria” (“Умови відбору”)
from combo list boxes.
2. The type of report is specified. On the form “Formation of documents and reports”
(“Формування документів /
звітів”) a report is selected from drop-down list in
case it is needed to form the list of tasks, or corresponding flags are ticked
and “Form the documents list” (“Скомпонувати список документів”) button is pressed in case is
needed to form a document.
. Report is formed for viewing and printing or
exported into an *.rtf file, depending on the state of “Create *.rtf file” (“Створити файл *.rtf”) flag on the form
“Formation of documents and reports” (“Формування документів / звітів”).documented reports can be used as
post instructions. And in such case these instructions will cooperate different
departments in achieving the global goal, such as international standard
implementation.reports of the ISMS “Matrix” demanded the development of several
custom functions. The listing of the program module for the report “All tasks”
(Всі задачі) is presented in appendix
F as an example.
3.6.3 Risk assessment
The risk assessment function is realised by approximate
estimation mechanism.
1. First, the assets to be protected are defined and
entered into the ISMS in the form of assets list. Each asset is assigned a loss
value (збиток) i.e. approximate loss
estimation in case of asset failure.
2. Next, the whole scope of threats typical to
organisation in question is entered into the ISMS in the form of threats list.
Each threat is assigned a frequency value (частота) i.e. approximate scaled estimation of appearance
frequency.
. Finally, the risk list is formed by assigning
threats to assets. This step is put instead of cross-joining assets with
threats because many minor or even impossible risks may be formed (like
physical damage to intellectual capital). The risk values are obtained
automatically from multiplication of asset loss value by threat frequency
value.are assigned automatically to tasks and document records when
corresponding pair of asset and threat are stated in classification
fields.pivot risk chart “Оцінка ризиків” (“Risk
assessment”) provides the overview of
the risks faced by organisation and asset-threat distributions with overall
estimations by each asset and each threat.
3.6.4 Information security policy
formation
The work [2] presents the definition of the IS policy as:
“the set of
laws, rules, recommendations and practical experience that determine the
administrative and project decisions in the information security sphere. The IS
policy determines the
organisation of management, protection and distribution of critical information
in the system. It must encompass all the features of information processing
procedures, determining the behaviour of the protected information system in
different situations”.work [2] also states that the information security policy
can cover one of the three following levels:
1. Higher level - statements affecting organisation on the whole, having
general character and, as a rule, coming from the management of the
organisation;
2. Middle level - issues that cover the separate
aspects of information security, but are important for the different systems applied in the
organisation;
. Lower level -
covers concrete
services, including the two aspects - purposes and ways of their achievement,
thus being the most detailed.common practice of creating the IS policies in
commercial organisations limits to having two policies: a high-level and a
low-level ones. The former describes the general goals of the IS in the target
organisation, and the latter contains the detailed descriptions of the concrete
technical means and measures.ISMS “Matrix”, as one of its main functions, can
produce the high-level IS policy, classifying all the present knowledge. The
knowledge elements in the document are grouped in the following order:
1. By directions of the target organisation’s IS;
2. By threats corresponding to each of the directions;
. By measures aimed at counteraction to these
threats., classical threat-counteraction model is preserved while complying
with the system approach to IS. Plus, the formed IS policy complies with all
the IS documents considered in the target organisation (i.e. registered in the
ISMS).
The contents of the policy document is composed of the
information contained in the fields “Description” (Опис) of the knowledge section of the ISMS, so it is important to
fill these fields when entering the document sections or knowledge elements.
The recommendations concerning the contents of the field are presented in
subsection 3.4.3 “Main data storages”.information security policy in the ISMS “Matrix” is
formed by pressing the button “Form the information security policy” (Сформувати політику
інформаційної безпеки) on the form “Formation of documents or reports” (Формування документів / звітів). The sample page of the formed IS
policy is presented in appendix D. The sample IS policy is formed of several
bank IS documents, including [3] and [4]. It is possible to add official
introduction to the IS policy template.
Conclusions to section
developed product is an information security management
system (ISMS) capable of producing documents like information security policy
or operational reports and performing statistical analyses from various
perspectives. The ISMS operation is based on input knowledge about the target
organisation and other documented knowledge on IS, ISS and IS management.input
elements of the product are the following:
. Information about the target organisation;
. IS standards;
. Normative documents;
. Knowledge;
. Standard post descriptions;
. Operational tasks statements.information about the
target organisation is presented by the sets of elements arranged in accordance
to the system approach to IS. The content of the element sets represents the
known structure and peculiarities of business processes in the organisation.IS
standards that are implemented (or intended to be) in the target organisation
are stored in the knowledge section of the ISMS.normative documents are the
legal papers concerning IS in the target organisation, like national law about
confidentiality or enterprise regulation.other available knowledge about IS may
include the results of the latest research in the field, or the best
practices.standard post descriptions are general rules for a position in a generic
company accepted broadly. It sometimes happens that such descriptions do not
completely fit into a certain organisation. Nevertheless, they are perfect
reference for the production of the customised post descriptions.operational
tasks statements are the current tasks set by the management. They can be
concrete or describe the main functions of the officials.on the input
information classified according to the system approach to IS, the outputs of
the developed ISMS include the following:
. Information security policy;
. Statistical analyses;
. Operational reports.high-level IS policy is formed
by the developed ISMS of all the available knowledge. It is the set of general
laws, rules, recommendations and practical experience that determine the
administrative and project decisions, affecting the organisation at the
top-management level. The formed IS policy describes the general goals of the
IS in the target organisation.statistical analyses present the various
distributions of tasks and knowledge that could be used in the internal audit
procedures. The pivot charts display the general overviews of the IS state at
the target enterprise from the different perspectives.operational reports on
tasks can be used as analytical documents or post instructions cooperating
different departments in achieving the common goal.add certain functions, the
program modules were written (see appendixes E, F).
CONCLUSIONS
In the section 1 of the work the issues of information
security management in corporate networks were explored. The results of the
latest investigations in the branch, including the ones performed by the
author, were overviewed. The general task of information security management
system development was formulated.information about the normative documents
guiding the information security management in the world and in Ukraine was
presented.results of analysis of the present information security management
solutions were provided. The most integrated solution in the Ukrainian market was
considered.mathematical model of information security system state was
described as a continuous process with random parameters.the section 2 of the
work the demands to the information security management system (ISMS) were
reviewed and the features needed in an effective information security
management product were formulated.information security management system was
developed according to the formulated task and defined effective ISMS
features.database structure was developed to contain the knowledge on
information security and operational tasks. Each of these records is placed in
the framework of the system approach to information security by the classifying
elements.program modules were developed in Microsoft Visual Basic for
Applications language (MS VBA) to support the custom functions of the forms and
reports in the ISMS.the section 3 of the work the detailed description of the
product structure, interfaces and operation was presented. The fragment of
generated high-level information security policy was presented as the ISMS outcome
example.solutions of the twelve major problems in analogous information
security management products and the improvements made by the developed ISMS application were
presented.
The financial advantages of the developed ISMS application
were estimated.
Due to scarcity of resources devoted to the development of
the ISMS “Matrix”, wide encompassing of IS management processes is compensated
by inability to operate at lower technical levels (for example, collecting or
analyzing log files). To compensate these challenges and accelerate the
development of the product, it is needed to invest money to support the
developers or devote a professional development team.
The ISMS “Matrix” is capable of gaining economical profit to
its developers. The product is developed as a freeware, but the income is
obtained from providing the consulting, support and customisation of the
product.
The author (and developer) of the ISMS “Matrix” continuously
collects the feedback from its users to ensure the performance stability and to
determine the necessary development trends. According to the latest demands,
the following development perspectives are defined as necessary.
1. Development of the out-of-the-box content for most
demanded Ukrainian and international standards, as well as for widespread types
of enterprises;
2. Improvement of the method of internal IS audit
execution to develop more clarity in IS state vision by the organisation’s IS
managers;
. Creation of an expert system to provide more
decision making support;
. Creation of the informative help and reference
system;
5. Improvement of the educational functions to increase
the level of trained IS specialists;
. Improvement of the personnel management functions,
like tracking of tasks with several consecutive responsible persons;
7. Easy and comfortable adjustment of any reports,
charts and diagrams;
8. Creation of wizards that will guide the users
through the initial stages of exploitation.
REFERENCES
1. Information
technology. Security techniques. Information security management systems.
Overview and vocabulary [Text]: international standard ISO/IEC 27000:2009(E). -
Switzerland: ISO/IEC, 2009. - 26 p.
2. Домарев,
В.В. Безопасность информационных технологий. Системный подход [Текст] / В.В.
Домарев. - К.: ООО «ТИД «ДС», 2004. - 992 с.
3. Інформаційні
технології. Методи захисту. Система управління інформаційною безпекою. Вимоги
(ISO/IEC 27001:2005, MOD) [Текст]: ГСТУ СУІБ 1.0/ISO/IEC 27001:2010. - К.:
Національний банк України, 2010. - 49 с. - Код УКНД 35.040.
. Інформаційні
технології. Методи захисту. Звід правил для управління інформаційною безпекою
(ISO/IEC 27002:2005, MOD) [Текст]: ГСТУ СУІБ 2.0/ISO/IEC 27002:2010. - К.:
Національний банк України, 2010. - 163 с. - Код УКНД 35.040.
. Про
набрання чинності стандартами з управління інформаційною безпекою в банківській
системі України [Текст]: постанова правління Національного банку України від 28
жовтня 2010 р. № 474. - К.: Національний банк України, 2010.
. Domarev,
D.V. Information security management system “Matrix” based on system approach [Text] / D.V. Domarev // Тези доповідей ХІ Міжнародної
науково-практичної конференції студентів та молодих учених «Політ. Сучасні
проблеми науки»: м. Київ, 6-7 квітня 2011 р. - К.: НАУ, 2011. Т. 1. - С 70.
7. Domarev, D.V. Analysis of Ukrainian legal
documents on providing information security [Text] / N.A. Vinogradov, D.V. Domarev // Наука і молодь. Прикладна
серія: Зб. наук. пр. - К.: НАУ, 2007. - № 7. - С. 78 - 81.
8. Домарев,
Д.В. Применение полумарковских процессов в разработке и описании состояния
систем защиты информации [Текст] / Д.В. Домарев // Системи обробки інформації. Безпека
та захист інформації в інформаційних системах.: Зб. наук. пр. - Х.: ФОП «АЗАМАЄВА В.П.», 2009. - № 7(79). -
С. 19 - 24.
9. Domarev, D.V. Information security management
system “Matrix” based on system approach [Text] / D.V. Domarev // Проблеми інформатизації та
управління: Зб. наук. пр. - К.: НАУ, 2011. - № 2(34).
. ISO/IEC
27001 certification standard - ISO27k Forum [Electronic resource]. - Access
mode: http: // www.iso27001security.com/ html/ 27001.html.
. ISO/IEC
27002 code of practice - ISO27k Forum [Electronic resource]. - Access mode:
http: // www.iso27001security.com/ html/ 27002.html.
12. Proctor,
P. MarketScope for IT Governance, Risk and Compliance Management [Electronic resource]:
Gartner RAS Core Research Note G0017S755 / P. Proctor, M. Nicolett. - Access
mode: http: // www.gartner.com/ DisplayDocument?id=1361628
. Lumension®
Endpoint Management and Security Suite Datasheet [Electronic resource]. -
Access mode: http: // www.lumension.com/ Media_Files/ Documents/
Marketing---Sales/Datasheets/Lumension-Endpoint-Management-Security-Suite.aspx.
14. Howard,
R.A. System analysis of semi-Markov processes [Text] / R.A. Howard // IEEE
Transactions on Military Electronics - New York: Institute of Electrical and
Electronics Engineers, 1964. - Issue 2, vol. 8. - P. 114-124.
. ISO/IEC
27000 series FAQ - ISO27k Forum [Electronic resource]. - Access mode: http: //
www.iso27001security.com/ html/ faq.html.
16. Salah,
O. Mandatory Information Security Management System Documents Required for
ISO/IEC 27001 Certification [Electronic resource] / O. Salah, G. Hinson. - Access mode:
http: // www.iso27001security.com/ ISO27k_mandatory_ISMS_documents.rtf.
Appendix A
Fig. A.1. The logical deduction hierarchy of ISS
security level estimation
Appendix B
The
solutions of the problems in analogous products by ISMS “Matrix”
|
Problem
|
Solution
|
|
The product is
concentrated more on assessment, than on managerial functions
|
The main
function of the “Matrix” is high-level management
|
|
No conditional
branching in workflow algorithms
|
Workflow is not
limited to business processes with strict algorithms
|
|
Limited
flexibility in self-assessment
|
The operation of
the “Matrix” is based on self-assessment data and is dynamically rebuilt
according to any changes
|
|
Products may be
concentrated on a single standard and not appropriate for broader use
|
System approach to
IS enables handling of any normative documents - from internal regulations to
international standards
|
|
Cost is
considered high by customers and evaluators
|
The price is in
average 10 times lower than in analogous products because: 1. The system core
is distributed freely; 2. Support pricing is low due to immaturity of the
product.
|
|
Content is all
based on bottom-up, IT-centric control management requirements
|
The “Matrix” is
designed to operate only on high managerial levels, preventing from drowning
in the vast amount of technical details. Thus overall clearance is maintained
|
|
The maturity of
the products makes their interfaces complex for users
|
Interfaces can
be customised on demand for each customer
|
|
End users have
reported configuration difficulties
|
No configuration
needed, except allowing MS VBA macros
|
|
No predefined
security policies
|
System filling
with any normative document or policy is available from product support unit
on demand
|
|
Mostly
compliance reporting with only a light treatment of risk
|
Risk assessment
is a dedicated function, providing both detailed risk estimations and pivot
table
|
|
Development of
policy and control framework content for commercial regulations
|
The system
approach to IS is equally effective in both state and commercial organisations
|
|
Limited audit
support
|
The variety of
reports and pivot charts allows passing most audits without reassessment
|
Appendix C
Database
scheme
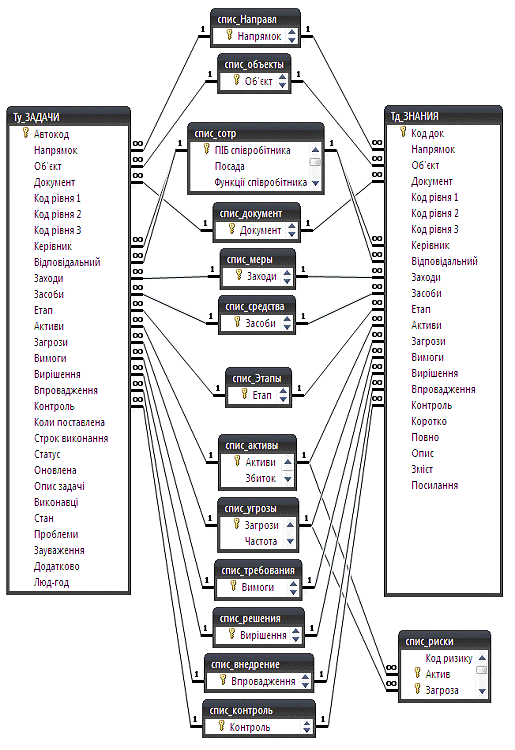
Fig. C.1. Database scheme of the ISMS “Matrix”
Appendix D
Excerpt
of the IS policy formed by the product
Політика інформаційної безпеки верхнього рівня - генератор
документів бази знань СУІБ "Матриця"
Напрямок: Банк в цілому
Загроза: Загрози Комп'ютерній мережі
Заходи: 06.2.1 Ідентифікація ризиків
4.1 Оцінка ризиків безпеки
Оцінка ризиків повинна ідентифікувати і визначити величини і
пріоритети ризиків в залежності від критеріїв прийняття ризику і суттєвих цілей
організації.
Національна примітка.
Банки України використовують декілька програмно-технічних
комплексів автоматизації банківської іяльності, які постійно обмінюються
інформацією, тому галуззю застосування оцінки ризиків повинен бути весь банк в
цілому.
Напрямок: Банк в цілому
Загроза: Втрата цілісності
Заходи:
.1 Внутрішня організація
Ціль: Управляти інформаційною безпекою в організації.
Напрямок: Всі напрямки ІБ
Загроза:
Заходи: 06.2 Зовнішні сторони
6.2 Зовнішні сторони
Ціль: Підтримування безпеки інформації організації та її
засобів оброблення інформації, до яких мають доступ, обробляють, якими
управляють або з якими підтримують зв'язок зовнішні сторони.
Безпека інформації і засобів оброблення інформації, які
належать організації, не повинна знижуватись через введення в експлуатацію
продуктів або послуг зовнішньої сторони.
Будь-який доступ до засобів оброблення інформації
організації, а також оброблення та передавання інформації зовнішнім сторонам
повинні бути контрольованими.
Якщо є бізнес-потреба в роботі з зовнішніми сторонами, яка
може вимагати доступу до інформації або засобів оброблення інформації
організації, або в отриманні від зовнішньої сторони чи наданні їй продукту та
послуги, повинна виконуватись оцінка ризику для визначення вимог контролю та
наслідків щодо безпеки. Контролі повинні бути погоджені та визначені в угоді з
зовнішньою стороною.
Напрямок: Всі напрямки ІБ
Загроза:
Заходи: 06.2.1 Ідентифікація ризиків
4.2 Оброблення ризиків безпеки
До початку оброблення ризику, організація повинна встановити критерії
прийняття ризиків.
Для кожного з ризиків, ідентифікованих після оцінки ризику,
треба прийняти рішення щодо
оброблення ризику.
Визначити підхід організації до оцінки ризику (4.2.1.c
Розроблення СУІБ)
Appendix E
Program
module of the shared ISMS functions (listing)
Option Compare Database
Function IsFormOpen(fname As String) As Boolean
'check if a form is openedError GoTo ErrFormOpenfrm As
Formfrm = Forms(fname)= TrueFunction:
IsFormOpen = FalseFunction
Sub openRiskPivot()
'open pivot chart of risk estimations from main menu.OpenForm
"Ф_своднОценРиск", acFormPivotTableSub
Sub showArchived(rname As String)
'get current report's name
Dim rep As Report
Set rep = Reports(rname)
'check if need to show arcived(Forms![Ф_фильтры].[Флажок_показАрх]
= 0) Then
rep.Filter = "NOT([Статус] = 'Архівна')"
rep.FilterOn = True: rep.FilterOn = FalseIfSub
Sub hideParam(rname As String) 'hide text fields in head
'get current report's name
Dim rep As Report
Set rep = Reports(rname).Титул_изм.Visible =
False.Надп_титул_изм.Visible = False.загол_изм.Visible =
False.Надп_загол_изм.Visible = FalseSub
Continuation of appendix E
Public Sub hideDates(rname As String) 'hide date fields in
head
'get current report's name
Dim rep As Report
Set rep = Reports(rname).Титул_ПолеС.Visible =
False.Титул_ПолеПо.Visible = False.надп_Титул_2.Visible = False
.загол_ПолеС.Visible = False.загол_ПолеПо.Visible =
False.надп_загол_2.Visible = FalseSub
Sub filters_initiate(fname As String)
'get current form's name
Dim frm As Form
Set frm = Forms(fname).FilterOn = False
'hide filters
frm.Кн_закрФильтр.Visible = False
frm.Групп_фильтр.Visible = False
frm.Кн_обнов.Visible = FalseSub
Sub filters_show(fname As String)
'get current form's name
Dim frm As Form
Set frm = Forms(fname)
'show filters
frm.Кн_закрФильтр.Visible = True
frm.Групп_фильтр.Visible = True
frm.Кн_обнов.Visible = True
DoCmd.OpenForm "ф_фильтры"Sub
Sub filter_apply(fname As String)
'get current form's name
Dim frm As Form
Set frm = Forms(fname)
'apply selected filterCase frm.Групп_фильтр
Ending of appendix E
Case 1 'Ответственный
frm.Filter =
"[Відповідальний]=[Forms]![ф_фильтры]![сотрудник]"
Case 2 'документ
frm.Filter =
"[Документ]=[Forms]![ф_фильтры]![Документ]"
Case 3 'меры
frm.Filter = "[заходи]=[Forms]![ф_фильтры]![меры]"
Case 4 'средства
frm.Filter =
"[засоби]=[Forms]![ф_фильтры]![средства]"
Case 100 'Активы
frm.Filter =
"[Активи]=[Forms]![ф_фильтры]![Активы]"
Case 200 'угрозы
frm.Filter =
"[загрози]=[Forms]![ф_фильтры]![угрозы]"
Case 400 'требования
frm.Filter =
"[Вимоги]=[Forms]![ф_фильтры]![требования]"
Case 500 'решения
frm.Filter =
"[Вирішення]=[Forms]![ф_фильтры]![решения]"
Case Else 'disable
frm.FilterOn = False
Exit SubSelect.FilterOn = TrueSub
Sub filters_close(fname As String)
'get current form's name
Dim frm As Form
Set frm = Forms(fname)
'close filters.FilterOn = False.Кн_закрФильтр.Visible =
False.Групп_фильтр.Visible = False.Кн_обнов.Visible =
FalseIsFormOpen("ф_отчеты") Then
MsgBox "Фільтр вимкнено, але вікно усмов відбору не буде
зачинено, доки відчинене вікно компонування документів.", ,
"Попередження"
DoCmd.Close acForm, "ф_фильтры", acSaveNoIfSub
Appendix F
Program
module of the ISMS report (listing)
Option Compare Database
Sub Report_NoData(Cancel As Integer)"Інформація про
задачі відсутня.", vbOKOnly, "Звіт порожній"= TrueSub
Sub Report_Open(Cancel As Integer)Case Me.OpenArgs
Case "expired" 'expired tasks only
Me.загол_Надп.Caption = "Прострочені задачі на "
& Date
Me.RecordSource = "Зу_Срок"
Case Else 'no conditions. List all tasks
Me.загол_Надп.Caption = "Повний перелік задач"
Me.RecordSource = "Зу_всеЗадачи"
showArchived (Me.Name) 'call public sub on this
reportSelectSub